2008-09-01
Abstract
Having started up focusing on unwanted tracking behaviour, Lavasoft's Ad-Aware has gradually branched out to cover adware, spyware and now with the integration of a full anti-malware engine, the gamut of trojans, viruses and worms, with a selection of extras thrown in for good measure. John Hawes reports on how the product has developed to face the multi-pronged malware dangers of the modern age.
Copyright © 2008 Virus Bulletin
‘The Original Anti-Spyware Company’, reads Lavasoft’s tagline, and the company’s flagship Ad-Aware range is a grand old name with impressive brand awareness. The company is approaching its tenth anniversary, and as if to celebrate has created a spanking new edition of Ad-Aware with a host of upgrades and improvements.
Having started up focusing on unwanted tracking behaviour, the product has gradually branched out to cover adware, spyware and now with the integration of a full anti-malware engine, the gamut of trojans, viruses and worms, with a selection of extras thrown in for good measure. I was intrigued to see how the company’s products had developed from the fairly simple on-demand-only scanners of yesteryear, to face the multi-pronged malware dangers of the modern age.
Although many of Lavasoft’s users will be more familiar with finding the company’s products in the ‘most popular’ lists of various free download sites, Lavasoft’s main web presence is at www.lavasoft.com. From here, localized sites in a range of languages can also be accessed.
The homepage is simple and uncluttered, adorned with soft colours and the ubiquitous photos of attractive young men and women studiously fiddling with slick laptops. Easy-to-spot buttons direct would-be downloaders or purchasers to the product range. A prominent link promises discounts to non-profit organizations, and elsewhere links lead to details of the latest threats, blog entries and industry news articles, as well as a poll.
In the company information section I discovered that, though nowadays based in Gothenburg, Sweden, Lavasoft was in fact set up in Germany. Alongside a selection of similar nuggets of information on the firm and its history, the company blog and industry news section keep readers up to speed in the latest developments in security, along with some jocular cartoons on office life. An awards section boasts numerous entries, mostly from download sites recognizing the popularity of the free editions over the years; the product currently boasts 200 million users worldwide.
Probing deeper into the site brought me to the full product range, which includes several versions of Ad-Aware itself and much more besides. The bare-bones free version has several siblings – a ‘Plus’ edition, which includes the new anti-virus component as well as real-time protection; a ‘ Pro’ version, with even more extras and benefits, and an ‘Enterprise’ version, with multiple-licence options and a central management system. A personal firewall is also available – which has scored reasonable ratings on firewall comparative sites – as well as a range of other security and system-cleaning tools: a file shredder, a registry tuner, some backup and encryption systems. All are available from the company’s online shop, with the Pro version of Ad-Aware currently retailing at a fraction under $40 US. Support for several older platforms has been dropped, but the standard Windows 2000, XP and Vista (including 64-bit Vista), as well as Server 2003 , are all covered.
Support offerings include manuals, YouTube-style videos and FAQs for the users of the free version. The FAQs are fairly exhaustive and most seem clear and lucid. A fairly sleepy forum is also provided to keep the free users out of trouble. Users of the paid versions are granted access to an email form for submitting technical queries. I used this form to submit a fairly tricky request in the middle of a weekday, and received a response less than ten minutes later.
A brief glance through the manual showed it to be clear, lucid and thorough. Fairly wordy but with plenty of illustrations and helpful screenshots, it clearly marks which of the functions are restricted to certain product versions, to save users of the free version from unnecessary bafflement and jealousy. Rather a lot of acronyms are used – which are all clearly explained when they first appear, but mean the manual is better suited to a full read-through rather than as a quick reference to specific sections.
The next tab on the website, the ‘Security Center’, provides a wealth of handy resources including the standard latest threat list, glossary of terms, research team blog and sample submission system. More peculiar to the site are the wide range of simple guides, how-tos and white papers on various aspects of security and privacy, which are written in a clear and friendly style and spiced up with quizzes, polls, interesting statistics and so on (though data sources are often vague or ‘estimated’ – one unlikely claim was that as many as 37% of people actually read EULAs before accepting them). One of the major subsections in this area is titled ‘Threat Analysis Index’. I assumed this would be some form of malware encyclopaedia, but a quick look inside showed it to describe a risk-rating system on a sliding scale of 0 – 10, green to red. The name of the system was shortened to ‘TAI’ – an acronym I had seen sprinkled liberally throughout the manual.
Having managed to get hold of a full copy of the product, installation proved a pretty rapid and straightforward process. I had a good look through the EULA, but spotted nothing untoward, and everything seemed good to go in a pretty respectable amount of time. However, once the complex licence code was entered a lengthy process of downloading and installing got under way. A few false starts were accompanied by error messages which appeared behind the splash screen, warning that the update server was busy and could not be accessed. Watching the process trundle along gave me some hints as to the source of Lavasoft’s new virus detection capabilities, more on which later.
Eventually things were up and running, and a clean and slick interface was presented. This provided some details on the update and licence status as well as recent scan results, with a row of options down the left-hand side. The top bar drew attention however, with its warning that real-time monitoring was not active. Some investigation showed that the ‘Ad-watch’ module, which provides this protection, is not active by default, but can be started either from the main GUI or from a second desktop shortcut, which opens its own separate interface. It can be set to fire up on system startup, but again this is not the default, a choice presumably influenced by the product’s history as a standalone scanner commonly used in tandem with other anti-malware protection.
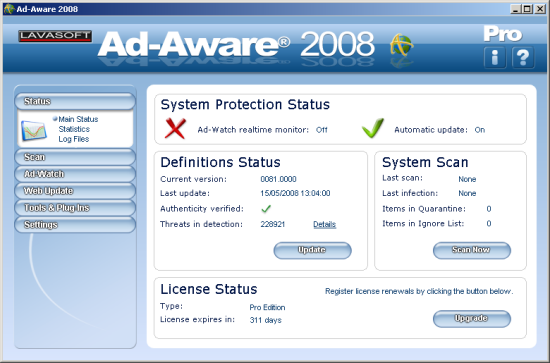
The system used for much of the testing was perhaps a little underpowered, towards the lower end of the requirements specified by the vendor, and as a result the flashy animation of the option bars acted rather slowly, as did some other aspects of the interface, especially the initial startup. This attempted another update each time it was opened, and I became more than familiar with the accompanying splash screen during initial exploration of the setup.
The selection of items on offer is pretty straightforward, with a scan tab providing a ‘smart’ scan targeting important system areas, a deeper version covering the whole machine and a customizable scan (not available in the free version). The ‘Ad-watch’ tab provides control over the various areas being monitored, including the registry, browsers, cookies and so on. Update and settings areas provide the obvious controls over updating and general behaviour, including the increasingly popular option to modify the appearance of the interface, with a hot pink look among the most appealing on offer. Finally, a section entitled ‘Tools & plugins’ provides some extra functions, which will be probed in more detail later.
Despite the sluggishness of the interface, some initial scans on a clean system zipped through their business at impressive speed, and running for a spell with the real-time protection enabled produced no noticeable slowdown even on a tired and underpowered test machine. Moving into the lab, a system riddled with adware and more serious nasties was scanned, and everything selected picked up without difficulty. Presentation of the scan results included a selection of scary icons for the different types of threat, and a colourful bar to indicate the seriousness of the danger presented.
In another nod to the product’s past in a slightly different sphere than the more traditional anti-virus products, the results are presented as a simple list of discoveries, with an empty check-box next to each. They can thus be selected for removal or left as they are, granting considerably more choice to the user than I would normally expect to see. Once each box had been checked, the process of cleaning, deleting or quarantining items was over in a flash, and highly effectively too, with all but the most innocuous registry changes and harmless files left behind as evidence of infection.
In some cases the presentation of scan results becomes a little awkward. Running some custom-designed scans over some of the VB test sets, I found scanning seemed to stop when it hit 5,000 items detected, with a message warning me of an exceptionally large number of infections which should be dealt with before proceeding. While this kind of number of infected items is not unusual for systems in the VB lab, the average user is unlikely to reach such desperate straits, at least not without seeing their machine collapse under the pressure, so the limit is perhaps justified, but it would make it a little difficult to push the product through a full VB100 comparative review.
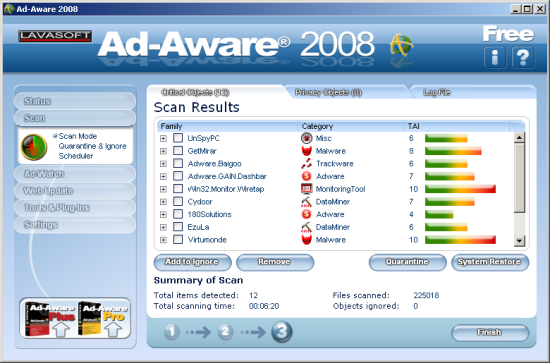
The colourful presentation of the outcomes in the main interface only provides an infection ID and severity indication, but a separate tab is presented at the end of the scan with more details, including a list of affected files and so on, with the empty check-boxes making an appearance to pick which items to clean up. There seemed to be no option to scroll sideways here, and with lengthy paths and more detailed detection names I found it very difficult to find much information. Looking over the more useful logs produced afterwards showed the same excellent detection results, and confirmed my suspicion that the anti-virus component has been licensed from Avira, whose AntiVir products are regular high achievers both in VB’s tests and those of other independent testing bodies. This engine seems a very wise choice and appears to be integrated quite seamlessly alongside Lavasoft’s own technology.
Another issue which might prove tricky should this product appear on the VB100 test bench any time soon, is the on-access component. Not being switched on by default after installation, and requiring specific user intervention to activate it, cause the product to fall outside the strictures of the test procedure.
The setup, like that of many products emerging from the anti-spyware sphere, does not have the option to check files on all forms of access, such as reading or writing, but instead waits for full execution before stepping in. However, this proved more than adequate to prevent infection from a random batch of samples I tried to run on the machine, which were all stopped in their tracks. Once again, an option to allow the detected files to run was presented to the user, much in the style of a firewall alert. Some brought up a selection of other alerts for suspect behaviours such as attempts to modify important sections of the registry, and in a few cases a single sample brought up half a dozen or more prompts for decisions, but none were allowed to carry out their malicious activities unchecked.
Some further exploration of the on-access configuration options dug up the ability to switch off the prompting and simply block anything judged as malicious. A contextual menu in the on-demand scan results provides the option simply to check all items, as well as a link to further data on an individual malware type. Further controls over the level of threat deemed acceptable (the ‘TAI’ score) and the level of heuristics active in the detection engine are also available. A command-line interface to the scanning engine is included (in the paid version), which was not tried, but the documentation suggests that it provides a good selection of options.
Measuring scanning speeds and overheads also proved a little problematic, as without full web access for activation it was not possible to get the full version running on the standard test machines, at least not without some time-consuming transferring and modification of system images. On-demand scans also had a rather long preparation period, despite the already hectic period loading the interface, and on some occasions ran to over five minutes before scanning proper started. Having got past this stage enough times, some simple tests were managed and showed pretty decent on-demand speeds, not quite as splendid as those achieved by Avira’s own product, but more than acceptable nevertheless. These scanning speeds were considerably slower when scanning similar numbers of infected files, as detections spark some further checking of other areas, including the registry, which may be affected by an infection. On-access overheads were less intensive than those of products that check every file as it is read or written to, but some slowdown was observed when the main interface was up and running, particularly during its frantic startup period which regularly left the rest of the system pretty sluggish for a few minutes.
During standard operation on a live system, after a little adjustment away from the default setup, the product left me feeling pretty safe in day-to-day operations, and with a scheduled scan (again not available in the free edition) set up to probe more deeply at regular intervals, Ad-Aware provided a solid and reliable level of security. In order to set much of this up, fairly thorough reading of the manual or built-in help may be required – unfortunately there is no contextual access to appropriate areas of the help from specific sections of the product, which would have been useful.
Beyond the basics of broad-spectrum protection against malware and other privacy intruders, a few extra components are included in the product. This is not a full Internet security suite, but as the company also produces its own firewall, anti-spam and other technologies it seems likely that further development in this direction will appear fairly soon. For now, however, there are a couple of tools listed in the ‘Tools & Plug-Ins’ page.
The ‘Process Watch’ explorer tool provides a comprehensive list of running processes, along with child processes, activity and libraries in use, all with the option to terminate. This is fairly similar to the well-known Process Explorer tool from Sysinternals (now part of Microsoft), but presented in a slightly more friendly layout and with some less advanced options. It provides no warnings when attempting to shut down processes, and should probably be left alone by less confident users.
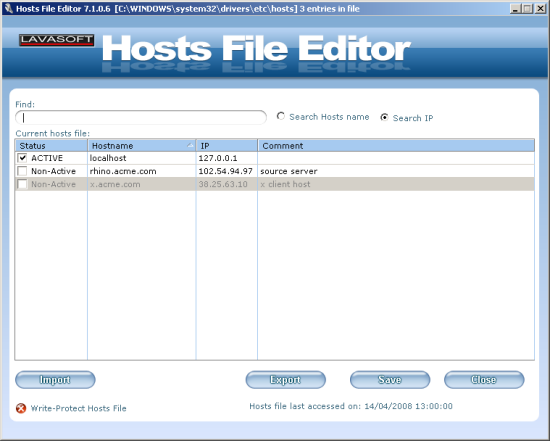
There is also a hosts file editing utility, which again provides a clear and shiny interface to the contents of the hosts file, and can be used by those with adequate understanding to remove unwanted entries and add new ones, to block access to specific areas for ‘parental control’ purposes. Again there is little guidance for those without the patience to read the manual entries, and those who already understand the use and layout of the hosts file will presumably be more than capable of making changes directly, but it is useful to have simple access to it from a central security tool.
Available from both the main interface and the secondary ‘Ad-Watch’ GUI is a section labelled ‘Track Sweep’, which monitors data stored by browsers and can be set to clear up any sensitive information, including cookies and browser history, at the end of a browsing session. This is available both as a real-time option, which by default only looks for known-bad settings, cookies and changes but can be set to erase all tracks for the paranoid, and also in the on-demand mode, to clean up as and when required. While these options are generally available in browsers themselves, once again it is handy for those with privacy concerns to have it all managed from a single point.
This is a pretty attractive product, combining leading detection technologies from the anti-spyware and traditional anti-virus worlds. The interface design is clear and eye-catching, if occasionally a little tardy to respond, and stability is excellent, with no errors or crashes spotted throughout the test period, other than the occasional, temporary issue connecting to the company’s busy update servers.
It provides solid and reliable protection with great flexibility available to the user. Perhaps the main issue I have with it is that it does require quite some user intervention to get the most out of it. Many of the pop-ups presented provide little information that would be meaningful to the average home-user, who is relied on to make sensible decisions fairly often both when malware is detected and when genuine software (including components of the regular updates to Windows provided automatically by Microsoft) attempts to make changes to sensitive system areas. Some fine-tuning of the setup is also required to ensure maximum protection, particularly the activation of the on-access protection as standard.
This is no simple set-and-forget product, but for the more technically inclined provides some good little tools alongside excellent detection and cleaning abilities. As I have said before in these pages, a little learning is an excellent thing, and all computer users should be encouraged to take an active interest in the dangers they face on the web, but for a total novice this product would perhaps present rather a steep learning curve. For those who know what they’re doing, it is certainly fit for purpose, and remains an excellent choice for what many have already long used it for: as a second layer of defence alongside another product - although the decision of which to have in place as the main on-access monitor has been made considerably less straightforward with the addition of the built-in real-time protection.
Lavasoft Ad-Aware 2008 was variously tested on: AMD Duron 1 GHz laptop, 256 MB RAM, running Microsoft Windows XP Professional SP3.
AMD K7, 500 MHz, 512 MB RAM, running Microsoft Windows XP Professional SP2.
Intel Pentium 4 1.6 GHz, 512 MB RAM, running Microsoft Windows XP Professional SP3.
AMD Athlon64 3800+ dual core, 1 GB RAM, running Microsoft Windows XP Professional SP2 and Windows Vista SP1 (32-bit).