2008-03-01
Abstract
John Hawes gets his hands on a preview version of the latest offering from AVG - AVG Internet Security 8.
Copyright © 2008 Virus Bulletin
I received an email this morning. It was nothing unusual – just another chain letter sent to VB’s hoax-reporting address by a scrupulous reader. I scanned through the message body, checking if there was anything to remark on. Nothing but the same old tragic tale and earnest plea to pass the message on for the usual vague reasons. When I reached the bottom of the text I found that a little note had been tagged on: ‘Scanned by AVG Free Edition’, it read. I scrolled a little further. There was another one, and another, and another. I counted 27 in all. Interspersed amongst them were a handful of legal disclaimers and the odd snippet of advertising from a webmail service. The tags of two other security products were present too.
Obviously, the incidence of a product’s marker within a many-times-forwarded hoax email is far from a scientific measure of market penetration – the message could have been through dozens of other filters and scanners that didn’t leave their footprint. But it did serve to drive home just how widely the name AVG has become embedded in the online world’s consciousness – in many minds an almost universal solution to security worries, thanks in great part to the roaring success of the free version of the product. Just why this should be is not entirely clear – there are other free anti-virus products available, quite a few of them in fact. But AVG, perhaps rivalled only by Alwil’s avast!, has achieved an extraordinary level of brand awareness on the back of its little freebie. Perhaps it’s all the free advertising it gets from email chain letters.
AVG does, of course, have much more to offer. The free edition is merely a taster, intended to get users familiar with the company’s products as well as its name, and encourage them to upgrade to the fuller-featured versions. The Internet Security suite is the most complete version, aiming to cover all the desktop bases, and is available to customers at all levels, from the home-user through small businesses to large enterprises, with targeted versions focusing on the needs of each. Like most of its competitors, AVG also provides a wide range of corporate products for its business customers, including server versions and support for Linux and FreeBSD – interestingly, these platforms are also covered by the home-user range.
Version 7.5 of the product has been around since late 2006, with the version number applied to the simple anti-virus as well as the more complex suites. Now version 8 is on its way, boasting a plethora of additions and exciting new functions, and I felt privileged to be allowed an early look at what it can do. Since this is a preview version, the product reviewed here is likely still to have a few wrinkles to be ironed out before the product’s final release – but it will provide a good idea of its potential.
The company behind the AVG product was until very recently known as Grisoft; the name was changed only a matter of weeks ago and this seems an eminently sensible move given the huge brand recognition the product has acquired.
For the time being www.avg.com still redirects to www.grisoft.com, but it seems more than likely that this situation will be reversed in the near future. At the time of writing this article, changes to reflect the new version have yet to be implemented on the web, the site currently focusing on version 7.5, with product information, manuals and support data for version 8 presumably still in the works.
The existing site has a pretty thorough range of offerings – the usual product summaries, marketing overviews and online purchasing of products backed up by more meaty stuff in the ‘Support’ and ‘Threat Info’ sections. Paying customers have access to 24/7 email support, with many products having built-in support connection functionality, and even users of the free edition are likely to find some helpful information in the decent FAQ section.
A selection of removal and cleanup tools are provided, the most notable of which is a bootable CD which includes a selection of handy tools for assisting with the removal of particularly nasty infections alongside a command-line version of the AVG scanner. This is an item most security admins and experts will have thought of from time to time, and many will have gone to various lengths to put together for themselves. It is a provision rather rarely offered by security vendors, possibly due to its limited use to inexpert users, and perhaps in part due to the licensing complexities of Windows. The current version does not support Vista systems, pending the integration of Windows PE 2.
The site also includes the obligatory virus encyclopedia, which seems reasonably well stocked if not quite up with the best of such offerings. One particularly nice touch, noted in several of the entries, was the inclusion of generic descriptions of the common techniques and tactics of types of malware where more specific details have yet to be added – something which many similar malware lists could do with in place of the more usual ‘no info here’ messages.
Although the corresponding versions for the latest product have yet to be released, a quick skim through the copious documentation provided for existing products shows a thorough level of information. A wide range of manuals cover the full product range, all written in a clear and straightforward style. It seems likely that the same will be the case when the details of the new release are finalised and added to the site.
AVG 7.5 included the basics of any Internet security suite – anti-virus and anti-spyware, a firewall and spam-filtering functionality. While many of the existing functions – including the interface, anti-malware engine and firewall – have been completely rewritten in the new version, several entirely new features have also been added. The major additions are an anti-rootkit scanner, previously available as a free standalone supplement, and advanced web-scanning technology, which comes from the designers of LinkScanner following AVG’s acquisition of Exploit Prevention Labs just a few months ago.
Despite the diverse range of functions, the installation process is fairly straightforward. The product was provided for review as an installer executable of around 50 MB which, when run, seemed to spend a few seconds contemplating its environment before getting the setup process under way. After offering a selection of languages, including most of the main European languages as well as Japanese and Brazilian Portuguese, a EULA clears up any legal issues the user may have. A choice of standard or custom installation is offered, with the custom option providing further choices as to install location, component selection (allowing the firewall, web filter and email filter/anti-spam components to be removed, and additional language support to be added) and finally email scanner setup – the default is the ‘personal email’ option, with plugins for Outlook and The Bat! also available.
The initial installation is followed by a number of setup steps. First, options for updating and scheduled scanning are presented. Updates can be scheduled to take place every four hours or once per day – but this would appear to be more of a rough guideline since, in testing the product during normal web usage, several update popups appeared over the course of an afternoon. The default scheduled scan is set for 12 noon, which seems a rather unusual choice, with most other products defaulting to the small hours of the night to avoid slowing the system down at peak usage times. Perhaps the AVG developers have great confidence in the small overheads of their product’s scanning, or perhaps they assume that most users will be installing the product on their home systems and going out to work during the day. With these settings adjusted to the user’s requirements, an initial update is performed and we are ready to move on to the firewall setup.
The first stage of this process is to select from a list of standard profiles – standalone, domain member or roving machines have their own sets of rules ready to go. This selection is followed by a scan of the system (which is configurable as to its thoroughness) to find any software that may need to connect to the web, and then the firewall is up and running too. An option is available to review the automatically selected settings in more detail.
Overall the setup seemed fast and simple, with even the various custom options unlikely to prove too taxing to any but the most uninformed user. Some excessive monkeying around with the firewall configuration pages did result in some odd effects – eventually disabling the firewall entirely without meaning to – but it seems likely that this is a minor bug that will be ironed out in time for the final release. A simple re-running of the config wizard soon set things straight, allowing me to move on to look at the new interface itself.
The main page of the new interface emphasises the full range of functionality on offer, with a very busy panel showing status information on 12 separate areas of operation. This may be something of an exaggeration of the scope of the product’s coverage however, since some of the areas seem to overlap. For example, the separate status buttons for ‘anti-virus’, ‘anti-spyware’ and ‘resident shield’ all seem to cover much the same thing, while items such as ‘licensing’ could perhaps be given less prominence. Each button can be double-clicked to access further information on that module. Double-clicking some of the buttons, such as those for anti-virus and anti-spyware, provides only more detailed status information, while others offer simple controls and basic settings.
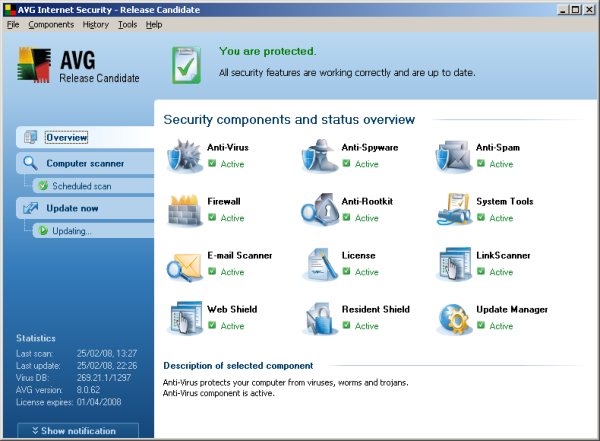
More in-depth fine-tuning is accessed via an advanced settings dialog, which can be opened from the menu bar. It would seem useful for more advanced users also to have this accessible from each module’s status page, linking through to the appropriate section of the advanced dialog, but perhaps such extra detail is considered likely to overwhelm users with more modest needs.
Also prominent on the main interface are some tabs down the left-hand side, which provide rapid access to on-demand scanning and the results of recent scans and updating. This seems sensible, as many users will simply leave the software running once installed, only visiting the interface in the event of something going wrong. Their first action in such a case is likely to be to ensure the product is up to date and to run a check of the system.
There was one final item at the bottom of the screen for which I could find less justification: a button marked ‘Notification’ which opened a little drop-down box. This seemed to have no function other than to display photographs of some handsome, smiling people – but it could be a means of feeding information on the latest threat outbreaks, which as yet has no data supply.
Probing into the product’s numerous functions, I started with those focused on the network boundary, preventing attacks and malicious code from reaching the protected system. The main form of such protection is the firewall, which seems pretty easy to set up with its clutch of standard layouts ready to apply and tweak at will. The scan for existing installed network software makes the setup task pretty straightforward, and the configuration interface seems very open and roomy, without the over-busy pages that sometimes pass as firewall setup systems. The product also features a gamer mode, which minimises the interruptions of the firewall alerts during gaming.
The suite incorporates a number of other protection features that block threats from penetrating the local system. Documents accompanying the preview copy of the product discuss in some detail the rise of the web to become the major vector for malware attacks, with mass-mailing worms subsiding somewhat in favour of trojans embedded in web pages awaiting unwary visitors. Of course, email is not neglected entirely, with the malware scanner checking incoming mail for attached nasties while the spam filter tries to minimise unwanted mails hitting inboxes. This area of the product was looked at only briefly, and there seemed to be no problems with the malware detection side of things.
More interesting and unusual are the web-filtering tools. The standard web anti-malware scanning functionality is found in many competing products, with files scanned as they are downloaded – in this case a maximum file size of 200 KB is set, but it can be scaled up to as much as 20 MB, though this is likely to have some hefty impact on download speeds, and presumably larger items are likely to be archives. The system also scans instant messaging traffic (ICQ and MSN).
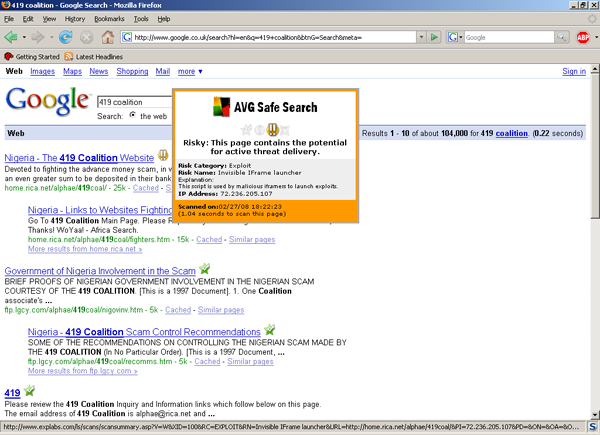
To further combat unintended file transfers caused by drive-by downloads, the new technology from Exploit Prevention Labs comes into play. This is implemented in two forms: a search scanner, which checks each link turned up by search engines, and a surf scanner, which checks pages for possible exploits. Both are integrated with Internet Explorer and Firefox. Unlike a lot of other web-filtering systems they operate on-the-fly, checking pages before they are visited, rather than using a database of known-bad sites.
The search scanner works with the big three search systems (Google, Yahoo! and MSN) and seems to process most pages of results in no more than 30 seconds (depending, of course, on connection speeds). Each link starts off being marked with a question mark flickering beside it, which turns into a comforting green tick when the page is deemed to be clean, or an angry red cross for pages considered to pose a danger. During web browsing, the surf scanner (‘Surf-Shield’) component watches out for embedded exploits and downloads. Both components seem to work pretty effectively, and had no trouble with a variety of well-known malicious items embedded in sites. There’s not much by way of configuration for these items, just on and off, and an option to report infected sites.
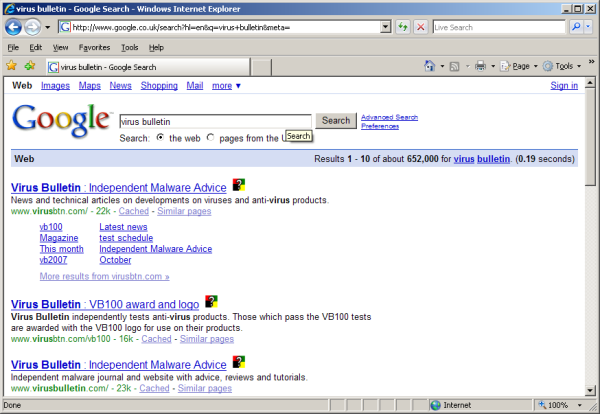
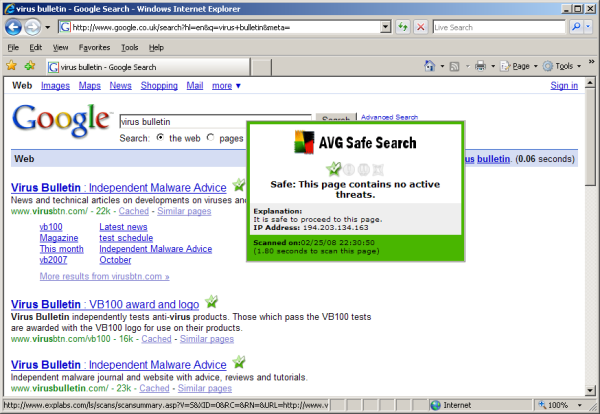
AVG’s detection rates have been pretty impressive for some time. Although not quite in the top league, the product has consistently scored extremely well in our VB100 testing, with almost all of the samples it has missed recently having been in the older and more obscure parts of the test sets. In other independent tests the product has fared even better, recently scoring some excellent ‘Advanced’ and ‘Advanced +’ ratings in AV-Comparatives tests. The product was awarded excellent marks from AV-Test.org too, with some ‘good’ and ‘very good’ ratings in the most recent multi-criteria test measuring response times and heuristics as well as signature detection.
Running the new version over our test sets showed similar detection rates, with barely anything going undetected even among the very newest items. AVG ’s scanning speeds have always been a little behind the fastest products in our tests, and running the latest build over the speed sets used in last month’s comparative produced some slightly slower times in most cases, with the on-access times similarly stretched. This can in part be put down to more thorough scanning settings, with several archive types delved into much more deeply with the new engine; changes to the running environment may also have played a part here. Memory usage seemed somewhat lower than previously, despite the numerous extra functions being rolled in, and even the slowest, most aged systems I tried it on seemed to suffer no noticeable slowdown with the product installed.
The product also includes anti-rootkit functions, which, as in most of these tools, operate separately from the main anti-malware scanner and require a separate scan to be carried out, although on-demand scans can be adjusted to include rootkit spotting. The scans seemed impressively fast and thorough – findings again confirmed by a major test carried out recently by AV-Test.org, which ranked the standalone version of the product very highly indeed, with excellent marks given for removal as well as detection. Installing the product on a system infested with some nasty stealth malware resulted in almost all of the system changes being repaired, although one item’s efforts to prevent removal by disabling registry editing remained a frustration.
Like the rest of the interface, the design of these areas is a lot more pleasant to use than in previous versions of the product (to my taste at least), and although configuration options in some areas are rather minimal there is plenty of fine-tuning for the average user.
A final set of tools is provided to round out a pretty full set. The ‘system tools’ section does not include anything enormously revolutionary – indeed much of its content is available elsewhere either as standard Windows tools or as free downloads, but here several useful items are brought together to keep all one’s security needs in the same place.
Tables of running processes, network connections, items auto-run at startup, browser plugins and extensions, and even DLLs providing layered network services, can all be displayed along with a handy button to terminate a process or connection, or remove an unwanted item. My only issue with this area is that it occasionally takes a few moments to populate the lists, and with no indication that such processing is under way some users may assume that the list is empty and move along, when in fact it simply hasn’t got around to displaying any information yet.
It seems that each time a new product arrives on the test bench for an in-depth review, a handful of entirely new ideas as to what should be in a security suite are discovered. Recently we have seen products with bundled data-shredding and encryption systems, advanced intrusion prevention, parental controls, backup and performance improvements, among many other items outside the basic requirements. AVG has added its own selection of items, of which the LinkScanner technology is perhaps the most unique and certainly the most interesting.
Of course, no product could hope to include all of these ideas in a single suite, but AVG has pushed the boat out considerably and bundled a lot into its package. On top of all the extras, the redesigned interface is a big plus – it now seems more rational and navigable, with a pleasant sense of integration across the various modules, all using similar language and layouts to create a smooth flow from one module to another.
Despite this being only a preview version, with some testing and fixes to undergo before it is released to the public, it showed very few wobbles even when put under pressure from some rather cavalier treatment – in fact it suffered fewer errors and glitches than many full release products that have made it to the VB test bench recently. The combination of a wide range of features – including some nice innovations – with much improved design and usability, stability, unexceptionable system impact and highly impressive detection, seems like a winning one, and I expect to see AVG continuing to go from strength to strength with this release.
AVG Internet Security 8 was variously tested on:
AMD K7, 500 MHz, 512 MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
Intel Pentium 4 1.6 GHz, 512 MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
AMD Athlon64 3800+ dual core, 1 GB RAM, running Microsoft Windows XP Professional SP2 and Windows Vista (32-bit).
AMD Duron 1 GHz laptop, 256 MB RAM, running Microsoft Windows XP Professional SP2.