2007-11-01
Abstract
The latest offering from ESET is a multifunction home-user product. John Hawes was given the chance to take a look at ESET Smart Security just days before its official release - and found a product which promises to be formidable competition for the range of security suites already on the market.
Copyright © 2007 Virus Bulletin
ESET has for some time been the small company with the big voice, making its presence felt in the early days through excellent test performances (both in terms of detection levels and speed), and more recently through a series of aggressive and stylish marketing campaigns. As a result, the company’s anti-malware product NOD32 has built up a strong and devoted following, particularly among more technically minded users for whom the idiosyncrasies of a rather unusual interface are more than outweighed by the product’s impressive power and low overheads.
Now, however, the firm is setting its sights firmly on the broader market. ESET’s latest offering, Smart Security (ESS), is a multifunction home-user product which promises to be formidable competition for the range of Internet security suites already on the market.
ESET was founded in 1992 in Bratislava, Slovakia, and now has offices in the US, UK, Argentina and the Czech Republic. The company’s flagship product NOD32 (these days officially known as NOD32 Antivirus System) has for some time been the top-performing product in Virus Bulletin’s comparative reviews – having amassed more VB100 awards than any other product.
Rarely missing a sample in any of the VB test sets, NOD32 also trounces its rivals regularly in speed tests, often leading the field by some considerable margin – and while recently some of those rivals have started catching it up, NOD32 remains among the very fastest month after month. These test results are confirmed by other independent bodies, with AV-Comparatives granting the product its ‘Best of 2006’ award.
So, with such a strong history and reputation, ESET presents an impressive challenge to its bigger rivals – one that, for many market watchers, has been held back only by the perceived ‘techiness’ of the product design. Though always incorporating some flair and panache, there has long been a hint of obscurity in NOD32’s GUIs, exemplified by the lingering use of acronyms for the various sections of the product – AMON for the on-access file monitor, IMON for the Internet guard etc.
With a new product aimed squarely at the broader, less technically minded market, and backed up by a new version of the detection engine, many have been eager to find out whether ESET has managed to shake off the techiness and produce a truly accessible interface to match the wonders of the technology beneath. I counted myself lucky to be among the first to find out.
ESET’s main website, www.eset.com, is an attractive place dominated by the company’s dark green colour scheme. The slightly spooky, sci-fi eye symbol of NOD32 features prominently, along with links to a 30-day free trial. The front page also carries details of the numerous accolades, awards and compliments received by the firm and its products, with the news section carrying details of a recent honour bestowed on the company’s San Diego-based US office for its recent rapid growth.
A graph of recent infections shows the malware trends seen over the last few hours, with links provided to the company’s VirusRadar statistics site, free removal tools and online scanner system. Like so many similar products, the online scanner system uses ActiveX and thus requires Internet Explorer (5 or later), along with all the associated risks of those technologies, but it does provide malware removal and detection of ‘potentially unwanted’ nasties.
Elsewhere on the site are the usual swathes of information on the range of products available, which cover a wide set of platforms including Microsoft offerings as wide apart as the aged DOS and the very latest Vista. File and email server editions are also offered, as well as centralized management and reporting tools in the enterprise versions.
Perhaps most interesting in this section are some pages comparing NOD32 with some of its rivals. A table shows NOD32’s considerable lead in the number of VB100 awards it has received, its scanning speeds as recorded in Virus Bulletin tests, as well as its unmatched record of not having missed any WildList samples in a VB comparative review since May 1998. Snippets from AV-Test and AV-Comparatives show a similarly impressive record of heuristic detection – something else for which the product is justifiably renowned – with both testing bodies rating NOD32 best in the field at spotting unknown threats with old signature databases.
Alongside areas providing trial downloads and online purchasing, the ‘Threat Center’ brings together various forms of information on the malware problem, with articles and white papers backing up some simple descriptions of malware types and the obligatory malware encyclopaedia. While not up to the standard of some of the bigger encyclopaedias provided by larger companies, and somewhat hampered by an inelegant layout, the encyclopaedia provides some useful information on a number of leading threats for those in need. The main page also carries links to the online scanner, a range of useful external malware resource sites and the VirusRadar site, www.virusradar.com, which features up-to-the-minute statistics on prevalence, new threats and outbreaks.
The company’s blog, also found here, differs from many vendor blogs in that it does not tend to focus on the latest discoveries, but instead provides a stream of insightful pieces, providing anecdotes, tips and advice on staying safe from malware and scams in the online world.
The support section provides a well-stocked FAQ and links to manuals and so on, as well as a support request form which promises free 24-hour response. A similar form is built into the product, enabling detailed system information to be sent along with the request, which can be configured and checked before sending. The new Smart Security product, due for release at around the same time as this review, is yet to be mentioned in any of these provisions. Experienced NOD32 users will know, however, that the true home of ESET’s support is the official forum hosted by Wilder’s Security, a busy place where queries of all types are answered rapidly by both fans and trained company representatives. This includes a section on the beta versions of the new product, which will presumably soon morph into coverage of the full release version.
As this product is so new, I was not able to see a full boxed version to check out the packaging, CDs etc., although I was given a preview of some very attractive cover artwork for the boxes. Instead, the product was provided in the form of two msi installers, for 32- and 64-bit systems; the packaging pictures revealed that there are to be separate home and business editions, for both ESS and the less complete but still potent package of NOD32.
The initial splash screens of the installer set the tone of the new product. The eye symbol used by earlier versions of NOD32 has been replaced by a very glossy and attractive symbol of the new world – a shiny silver android, shown in a number of pensive poses, representing the ‘intelligence’ of the scanning system, analysing files for unknown threats using those highly regarded heuristics.
Beneath this rather beautiful skin, little seems changed in the installation process, with the familiar questions about settings, updating and enabling various optional components.
These include the 'ThreatSense.net' system, which submits detections back to base to provide information on outbreaks as well as allowing new heuristic detections to be analysed more thoroughly, with full detection for new items then pushed back out to fellow users. There is also the option to enable or disable detection of ‘potentially unwanted’ files and products, neither of which is checked by default. Both of these settings can, of course, be changed later through the normal interface. The most taxing part of my first few installations was the entry of user credentials to activate the product’s licensing, but even these can be put off until later if desired, allowing for a trial install.
The setup process is fast and smooth, and the various requests for information put clearly and simply with little to worry about for the novice user. A more advanced setup process is also available for those who wish to fine-tune the likes of proxy settings, firewall configuration etc. from the off. In practically no time the thing was fully installed and ready to go, with no reboot requested, although in one instance, running 64-bit Windows Vista, this did seem to be necessary to activate the on-access protection fully (an issue that I understand has been fixed in the final release build).
With the main interface up and running, the change from the previous product is quite startling. Gone are the rather funky separable windows with their cryptic menu entries. Here instead is a much more conventional window, reflecting the general trend of such things and likely to be familiar in layout to anyone who has used a modern Internet security suite. Down the left-hand side are the major categories of information, starting with an overview of general protection status, indicating which modules are running at full power and accompanied by some simple figures on update versions, licensing and blocked attacks. Next is a scan section, where on-demand checks of the local system or individual areas can be run; an update area with more details on the latest detection data; and a setup page which allows quick changes to the operation of the product, such as password-protecting the controls, and switching on various parts of the functionality, including the on-access scanner and firewall. All of these are nice and simple, with no challenging technical jargon or overwhelming reams of numbers, and the layout is logical and easy to navigate. The functions offered are well thought out, catering for most of the everyday needs of the home user.
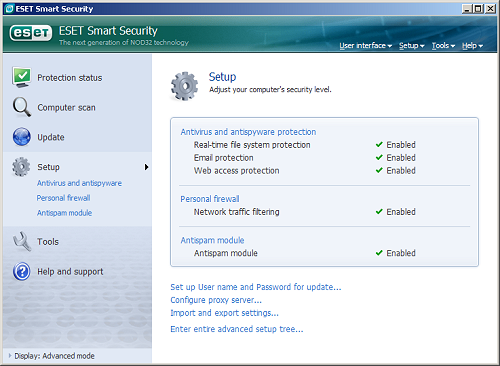
The interface can be flipped into a more advanced version, again using a simple and obvious button. This provides an extended version of the same set of pages, now subdivided where appropriate to access more detailed information and further control of the anti-malware, firewall and anti-spam subsections. An additional tab entitled ‘tools’ allows things like logging, quarantined files and scheduled jobs to be managed. Many of the control buttons in this area open up a new window containing the holy grail of configuration: the full setup pages for every conceivable area of the product, allowing the most dedicated fine-tuner to fiddle away to his or her heart’s delight.
There is configuration available here for all the standard aspects of the product. Scanning for viruses, spyware, trojans, etc. targets email and web vectors as well as standard files on disk and in memory (functionality that has been part of the NOD32 offering for some time), with Outlook monitoring set by default and other POP3 clients also supported. In the web filter, browsers and http ports can also be added and tweaked as needed, and software seen to be rendering clickable links (such as Microsoft Word) will automatically be counted as a browser and have its associated traffic watched over.
The whole thing seems pretty rational and nicely laid out, causing me only a few moments of confusion. The ‘cleaning’ mode of various modules is configurable only via a simple three-step slider, which offers a choice of no cleaning at all, ‘strict’ cleaning at the other end of the scale, and the default in the middle. As far as I could tell, the ‘strict’ mode deletes whole archives if an infected file is found inside, while the default does not, and the two are otherwise indistinguishable. However, the popups alerting the user to infected files offer more fine-tuning of actions, which can then be applied more permanently. The only other issue I had with the configuration pages was the apparent absence of tweaking for the right-click scanning mode, which was fairly prominent in earlier NOD32 versions (it could well have been in there somewhere, but was not immediately obvious). Of course, this sort of thing is of more interest to testers than to the average desktop user.
Help for this type of issue is provided of course, with the focus still firmly on the less experienced user. Everything is clear and simple, in plain language, and coverage is remarkably thorough. Links from within the product to the appropriate pages of the help are sparse, but seem present where most needed.
Scanning with NOD32 has long been one of the least arduous tasks required of a VB100 tester. With misses vanishingly rare, crashes and slowdowns similarly unlikely, and configuration systems invariably well-tailored to the tester’s needs, the product has long been something of a dream to work with. I must say that the new version took a little getting used to before its full potential could be unleashed. The simplified interface, even when toggled into the ‘advanced’ mode, offers little by way of configuration. Full system scans can be carried out fairly easily, and the right-click option allows for easy checking of individual files and folders, but for my somewhat specialist needs much plunging into the full setup page was required to ensure things were scanned as I wanted them to be. With the layout of this area easily mastered, however, this was no real chore.
A few scans of the VB test sets showed excellent detection ability as anticipated. The other striking aspect of ESET’s products, the superb scanning speeds, seemed if anything to have improved – scans blasted through in barely any time at all. Doing some further investigation into this phenomenal pace, I ran the product over the speed tests included in recent VB100 comparative reviews, comparing it with a version of NOD32 from a few months ago – of course, this is hardly a fair test, as those few months would have added much by way of detection data, and the new product has other things to do besides scanning. Remarkably, scans across most of the sets showed almost identical times despite the larger detection coverage of the new version, with some sets and platforms actually showing small improvements, like a sprinter shaving a few milliseconds off their personal best. The executable set and Windows Vista showed the most improvement, implying that ESET has been fine-tuning its scanning engine to focus on the most commonly infected items and what is almost certain (despite calls for boycotts in some areas) to be the platform of the future.
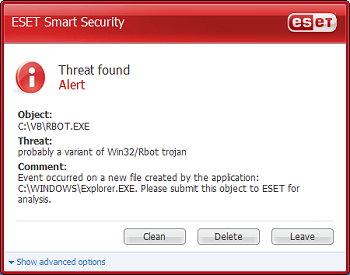
The heuristic capabilities of ESET’s product have long been highly regarded. They came through strongly again here, with large numbers of samples detected generically or as as-yet-unknown malware variants. The pensive android figure which adorns the product is intended to signify its built-in intelligence, picking apart files looking for suspect instructions, and at times, despite the speed, this could be seen in action. On a tiny handful of samples, including some in the latest WildList (released some time after the product was sent in for review), the infected files were missed, but on some of them the scan seemed to pause, looking extra hard at the file as if it had spotted something a little off but couldn’t quite put its finger on it. It seemed likely that if the heuristic paranoia level could be turned up a notch or two these files would have been labelled as suspect. Once passed by the scanner, some naughty behaviour, including placing files in system folders and initiating network connections, was then allowed – indicating that perhaps even with the product’s excellent detection rate a full-on intrusion prevention system, or more secure firewall settings, may be useful to fend off the very latest and most cunningly emulation-proofed threats. Retrying with a more up-to-date version showed all the missed samples were identified accurately and with ease.
The ‘ThreatSense.Net’ system tied in with the heuristics is designed to send samples of suspect files back to base for further analysis, providing group immunity and early warning of outbreaks. This is a technique which ESET adopted early on, and one which is becoming an increasingly popular and useful part of anti-malware products, as it allows for fast response to the ever-accelerating emergence of new threats. The behaviour of ESET’s system, including the quantity and type of data sent, is highly configurable and defaults to sending files during updating periods only, and checking for confirmation from the user first, but it can be set to send automatically as soon as a suspicious file is spotted.
Smart Security shies away from the ‘suite’ title so popular with multifunction products these days, instead preferring to be considered a single integrated whole offering several security services from a single point. Updates reflect this lack of modularization, making no differentiation between definition updates and improvements to the detection engine. The extra components, not featured in previous versions of NOD32 or the new one that is sister-product to this, are essentially the client firewall and spam filter.
The firewall is the biggest addition to the new product, having become pretty much a necessary part of any security product these days and something that is generally acknowledged as essential to safe networked computing. The default setting, chosen during installation, is ‘automatic’ mode, implying that the system decides what is safe and what is not. This approach has been tried by many products, generally needing at least a few screens of setup queries, and can be fairly successful, although there will always be some piece of software the developers missed out when setting up the default rules. The more standard tactic – prodding the user with popups every time a new item needs to connect to the network – is a more cautious approach, and there can be no denying that this method often only serves to frustrate people who don’t have the experience to understand whether a program can be trusted just from its filename.
The settings of the ESS firewall seemed admirably well-tuned, with ‘standard’ outgoing connections allowed after a little filtering and automatic blocking of inbound connections that have been initiated externally. The only question I received from the firewall, once I had allowed it to go along with the default automatic setting, was whether I wanted to allow filesharing within the local network, and even this was put in plain and simple language. Of course, more paranoid users, or those with less ‘standard’ requirements will want to investigate the deeper configuration, which is also possible.
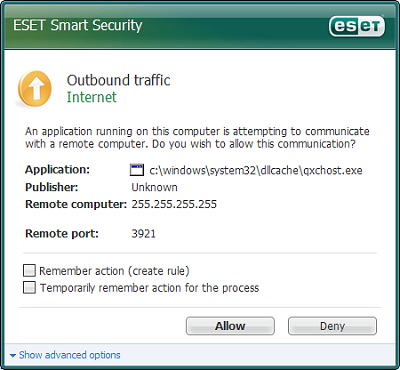
The firewall page of the main interface provides some handy buttons to shut down all network activity in an instant, or to disable the firewall completely, and full configuration is accessed via the advanced setup screen. Two further modes are available: an ‘interactive’ setting where users are prompted to allow or deny connections as they occur, with the usual option to create a permanent rule or simply allow a one-off connection, and a ‘rule-based’ mode where full sets of rules are defined in advance and applied to the letter, with anything not specifically allowed by the rules barred access to the network. Obviously, both require some technical knowledge of what is needed and what can be done without, but if configured properly should provide an even higher level of security. The firewall integrates with the web side of the malware scanner, so rather than blindly obeying the rules laid down traffic is monitored for malicious code passing through via normally permitted channels.
The anti-spam side of things is again pretty straightforward. A single page in the advanced setup screen allows some minor tweaking of the behaviour – actions on spotting spam, automatic whitelisting of addresses from local address books or from outgoing messages and so on, while a statistics page in the main GUI shows the number of emails processed and what was done with them. The system currently only supports Microsoft email clients Outlook, Outlook Express and Windows Mail, and has a standard training system to allow the user’s emailing behaviour to influence the basic filtering rules.
There are no additional bells and whistles here – not for ESET the hurried system clean-up tools, the encryption and data-leak prevention, or the tricky parental controls that are being bundled into various competing products. These things are, perhaps wisely, left to specialists in those fields. ESET concentrates instead on providing what it knows best: top-quality malware detection and removal, protection from the ever-growing deluge of nasties bombarding users via the web, email and unprotected networks. Items listed as modular extras in many other products, such as rootkit detection and advanced heuristics, are here quietly rolled in with the body of the product, as a necessary part of what it does rather than a tacked-on adjunct. The absence of a full-blown behavioural analysis or intrusion-prevention system is perhaps the only thing that seems significantly missing, and this seems likely to make its way into a future version of the product.
ESET seems to have upped the ante considerably here. While NOD32 has always been a cutting-edge product in technical terms, usability has seemed very much an afterthought in previous versions, at least as far as general users were concerned. In a sudden leap, this new product has shaken off the complexity and actually taken something of a lead in terms of ease of use. The default settings put in place in a few easy steps during the installation seem ideal for general purpose use, information and alerting is clear and helpful without ever seeming intrusive or scare-mongering, and detailed configuration is about as straightforward and painless as such things can be.
With the user experience reduced to an installation process, and possibly the occasional alert as another attack is spotted and blocked effortlessly, the unobtrusiveness is further enhanced by the product’s legendary lightning speed, miraculously unimpeded by the additional protection, keeping overheads to a level barely noticeable on modern high-powered systems. Lacking full behavioural monitoring may help minimize the slowdown, but with the level of in-depth analysis and emulation going on during scanning the performance is most impressive.
As vendors release their latest 2008 product ranges, the addition of new supplementary modules seems to be all the rage, most suites now sprawling with diverse functionality, often at the expense of user-friendliness and occasionally posing dangers of their own. ESET has resisted the temptation to sprinkle in too many extras, focusing instead on the core requirements of a security system. Covering all the essential bases with a smoothly integrated set of protective barriers, the combination of top-of-the-range detection, response time, heuristics and throughput with excellent presentation and design will make Smart Security pretty hard to beat.
ESET Smart Security was variously tested on:
AMD K7, 500MHz, 512MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
Intel Pentium 4 1.6GHz, 512 MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
AMD Athlon64 3800+ dual core, 1 GB RAM, running Microsoft Windows XP Professional SP2 (32-bit) and Windows Vista (64-bit)
AMD Duron 1GHz laptop, 256 MB RAM, running Microsoft Windows XP Professional SP2.