2006-05-01
Abstract
Matt Ham puts eTrust's ISS package through its paces.
Copyright © 2006 Virus Bulletin
CA (formerly known as Computer Associates) has been one of the lesser-known giants of the security software industry for a number of years – its products in this field being overshadowed both by other enterprise offerings and by boardroom antics.
In the past, Virus Bulletin has tended to concentrate on the enterprise-level versions of eTrust, which makes it something of a change, on this occasion, to review what can be considered a consumer-friendly package. The eTrust Internet Security Suite (ISS) combines several products within one package, the applications within it each being available as standalone purchases. As such, the product manifests itself in three main ways: through a central console, the individual application GUIs and, as has come to be expected, the Windows Security Center.
The applications contained within the package are currently eTrust EZ Antivirus, eTrust Anti-Spam, eTrust PestPatrol Anti-Spyware and eTrust Personal Firewall. This covers most of the security functionality that an average user would realise existed and, one hopes, desire to put into place.
The product was installed in a variety of ways, some more effective than others. In all cases, Windows XP Professional was used as the operating system, with Service Pack 2 applied. Most testing was performed on a machine attached to the Internet via an ADSL connection, though several installations were performed on an isolated network.
The isolated machines were used first, with the first test using a trial version of ISS. The installation process was accompanied by a few warnings due to the lack of connectivity. Eventually the suite seemed to have been installed successfully, with the exception of the anti-virus functions which were disabled. Installing a full version of the anti-virus application on top failed to remedy the situation, with the software declaring simply that the anti-virus engine did not exist.
This lack of anti-virus operation is not unheard of in CA's products – the Vet product, for one, refuses to operate if it has not been updated sufficiently recently. Since the anti-virus component within ISS is provided by the Vet engine, it is not unreasonable to suspect that the same feature is at work here. The presumed logic behind this is that users will attempt to update more frequently if their software is rendered useless otherwise. However, my suspicion is that most people are not likely to care so much about one more red blob on their task bar. With the situation far from useful for testing purposes, all further tests were performed on the Internet-connected machine.
The relative sizes of the software packages within ISS were intriguing, although at least the total package size was pretty close to the sum of its parts. ISS is a combination of eTrust EZ Antivirus (5.5 MB), eTrust Anti-Spam (2.5 MB), eTrust PestPatrol Anti-Spyware (13.5 MB) and eTrust Personal Firewall (8.0 MB). The combined ISS package amounts to 27.0 MB.
Although each of the single products was installed during testing, the process of installing the overall ISS package is covered in detail here. CA has ever been a stickler for licensing, and this applies equally to ISS, where a licence key request is the first interaction in the installation procedure.
It is noteworthy that a licence key is required not only for full products but also when installing demonstration versions. In addition, the demonstration versions are activated on the principle of a user supplying credit card details and then opting out later if they do not want to purchase the software. This is one of the more irritating ways of supplying demonstration software. On principle I would usually steer well clear of such demonstration versions.
Assuming a correct licence key is supplied, the next step is to specify an installation location. Following this comes the decision as to which of the four main components to install. For the purposes of testing all four were selected, although the test machine did not have any configured email clients present.
An installation progress box appears after this selection has been made, which lies dormant for a disturbingly long period before springing into action. At this point the user is bombarded by a rapid succession of additional progress bars erupting on the screen, as the components download updates. The PestPatrol updates seemed to take longest at this stage – perhaps not surprising given the relative size of the applications.
A further page of registration details also appears, which is dominated by a list of other products for the user potentially to be lured into buying. Since a reboot dialog eventually appears on top of this page, and the page is obscured by progress bars to a certain degree, this form of marketing is perhaps more subliminal than its designers would have hoped.
Any user completing the registration will, by default, be subjected to four different streams of email information – a service which I would have preferred to actively opt into, rather than out of. Rather than subject this registration page to even more abuse, however, rebooting to complete installation seemed a wise option.
The level of interactivity during the installation procedure so far is not exactly great. This seeming oversight is dealt with by the Configuration Wizard which now appears. During this configuration process the machine is isolated from any network connections, thus protecting the user during a potentially vulnerable period. As noted in the splash screen, the configuration process may be aborted at any time, resulting in the default security settings being applied.
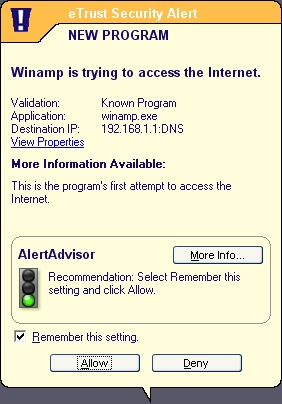
First to be configured is the Program AlertAdvisor, which is, in fact, the list of applications allowed to operate through the firewall as trusted entities.
An online whitelist is used here, which can be applied automatically, used as a recommendation for user decisions or simply not consulted, depending on the user's preferences. Although the automatic setting is the default here, I chose the user consultation setting in order to see what information this whitelist provided on various day-to-day applications. The setting proved to be rather irritating, in that permission was requested for every application I accessed – even the ones that I had whitelisted. I very quickly reverted to the less sanity-testing default setting.
The next two configuration settings are slightly less obvious, involving whether pop-ups, banners and cookies will be blocked and whether the Cache Cleaner function will be activated. I ignored both these settings, which default to being turned off in any case. With SP2 installed and FireFox as the primary web browser, popups have not been a problem on the test machine for some time. Likewise, disk space is not really a consideration and I have a natural distrust of applications that delete anything automatically – however much effort they may claim to save me.
This ends the firewall configuration procedure, after which a 'Tutorial' is launched through a series of ten dialog boxes. This is not entirely convincing, seeming just slightly too technical to be comfortable for a truly naive user, yet not offering much more advice than to follow the firewall's blocking recommendations when in doubt.
Next, the firewall dialog returns to configuration – offering all detected networks and asking whether these should be in the Internet or Trusted zone. I have my suspicions that the bulk of home users with a router will be confused as to whether this is a trusted or untrusted connection – thinking that the router must surely be trusted, as it sits just next to the computer in their living room. While the firewall has this process of post-install configuration, the other components are all set to defaults for later tweaking, so at this stage installation can be considered complete.
As a general rule, it seemed that installing ISS over other security products was not perceived to be a problem. Thus it was quite possible to run, for example, Windows OneCare, Microsoft AntiSpyware and eTrust Antivirus simultaneously with no warning messages appearing during the installation of the eTrust product. On the other hand, installing different versions of CA products does prompt warnings. This is especially noticeable since the downloaded versions have older definitions than a version installed on an Internet-connected machine that receives automatic updates. The result is that the user is bombarded with numerous, pretty much unavoidable, warnings that the application to be installed is older than the one currently running. It is reasonable to expect that some users will buy eTrust Antivirus and upgrade later to ISS, triggering these warnings in the process.
The warnings advise uninstallation before the addition of new versions, so this feature was also tested. Uninstallation was not a particularly arduous task, though it did require a reboot. To its credit, the uninstall facility removed all immediately obvious extraneous files, doing a better job than most such applications. On the other hand, reinstallation of ISS after it had been removed did not progress smoothly. Updating of the product did not seem to occur at all during the initial download period. Updating was therefore performed after the installation reboot.
ISS is designed primarily to be downloaded from the CA sales website and used without any hard copy being involved. A CD version is available, though this comes at an extra cost. As such, most users can be expected to be using product documentation in its online and soft-copy formats.
The degree to which documentation is supplied varies greatly between the products. For the firewall, for example, the tutorial represents the only easy-to-find documentation. Both the anti-virus and anti-spyware components have help files available from the Start programs tree, with an HTML readme file also being available for the anti-virus component.
The readme file demonstrates one particular weakness in many of the help functions I examined, in that it contains numerous hyperlinks to the main CA site. This is understandable, in that it means that the most recent versions of FAQs, howtos and other documents are always ready for use. Having to depending on a network connection for this information is, however, less than ideal. In case of a firewall misconfiguration or error it is entirely likely that the machine will have no active connection – there is even a specific 'panic button' which will cut the connection in case of suspected infections. Since contact details are also supplied via a web link, this could leave an already worried user feeling very isolated.
The readme does note that documentation is available in PDF format – despite this not being downloaded automatically. In this case, however, only a file name is given, rather than a download link. Such minor frustrations would put off many people instantly – myself included, were I not wearing my reviewer's hat. Sadly, there was no sign of the PDF in any easily discoverable part of the site and my curiosity was vanquished after a fruitless half-hour search. The lack of accessible documentation can hardly be said to be a high point in the presumed intention to make the product easy to use.
The help files were next to be examined, these being the most conveniently available source of documentation. It was quite a relief to note that the implementation here is very good. Full use is made of both internal and external links, though the internal links contain all the necessary product information that I required in my tests.
There is also a troubleshooting menu, which offers some good advice on how to deal with some common queries and problems. The only disadvantage here is that, as is usual with help files, it is very hard to print out a full manual for reference purposes. This should not really be necessary given the availability of the files for browsing, but may annoy some.
The usual CA corporate site at www.ca.com does not refer directly to ISS except though a succession of links. Links from within ISS, on the other hand, point to a sales site operated by a third party. This isolates the user from any useful information other than how to purchase further CA products. This is irritating at best, and downright frustrating if technical information is being sought.
The features available within ISS may be accessed easily in three ways: through the startling number of tray icons, by launching the applications individually, or through the use of the ISS central console.
Generally, the console offers a simpler view of the applications, with control over the functionality being limited. Status is well reported but, for example, the anti-virus and anti-spyware portions allow only a full system scan or update to be performed without recourse to launching the independent applications. While this simplicity does have some advantages, it would be nice to have at least the ability to scan a more finely tuned area of the machine, rather than the current all-or-nothing option.
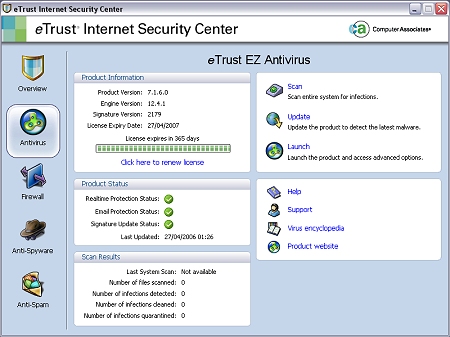
The firewall portion of the console is even more limited, offering status information, the option to launch the main firewall application and nothing else. The anti-spam application is unique in existing only through its tab in the console – though being listed as an individual application. However, anti-spam functionality was not tested at this time.
Once launched, the EZ Antivirus application has a rather more respectable number of options on offer. Four tabs control operations, divided amongst Virus Scanning, Update, Tools and Help. Help is dominated by version information, though it does also offer links to the CA website.
One of these links points to the Virus Encyclopedia, which is far more useful than the other links mentioned earlier. Here can be found the common fare of information on new threats, alerts and a variety of tools. Online scanning, sample submission, utilities and updates are available here. It would be more useful to have this as the primary product site.
The control offered on the Virus Scanning tab allows scheduling, scanning of browsed folders and the adjustment of settings. In reality, the settings that can be adjusted are limited to whether disinfection or quarantining will occur, and to the setting of exclusions. Updating is similarly streamlined, with schedules and proxies being the configurable areas.
Tools proved more interesting, offering views of quarantined items, logs and an overall system report for use if issues occur that require recourse to CA's technical support. The log viewer is interesting, in that its output looks far more easily parsed than that from CA's corporate products, which seems unusual. Examination of the raw log files proved that logging here is indeed in plain text, and thus eminently preferable to that of CA's corporate offerings.
The PestPatrol application, when launched individually, offers much the same level of control, though the gathering of prevalence data is also supported here. This collates, on a voluntary basis, the results of user scans in an attempt to provide wider statistical data. There is a large quantity of data available and Internet links are provided to this.
One unfortunate issue was that PestPatrol crashed twice while testing. The instability was limited to the GUI, however, with real-time scanning unaffected.
As a security suite designed for home use, ISS certainly contains all the standard features, plus a few which are less common, such as the privacy protection functionality.
Such a wide range of utility does, however, present problems to the developers when designing an interface. Since the ISS contains applications which can be installed and operated independently of one another, a single monolithic application is not really feasible. The situation is aggravated by the fact that the components have been developed by widely separated teams (originally by different companies).
From a more practical point of view, it would also be rather overwhelming for a potential user to be faced with all of the options available for each of the suite components. The use of a central console thus makes logical sense but I would suggest that it has not yet been taken far enough in ISS. The large number of tray icons is one example of the integration being not quite as deep as might be hoped.
On a less obvious note, updates are performed individually for each suite component rather than as conglomerated batches. This is most notable for the anti-virus and anti-spyware components which require frequent updates – often updates which cover the same malware. If the products involved had originally been developed in-house it might be feasible to use unified updates here but as it stands this would no doubt be an unpleasant technical challenge.
From a wider perspective, the gulf between the two types of detection is becoming increasingly blurred, such that it would perhaps make more sense to combine the two applications fully rather than have them perform the same operations, looking for the same files but independently. This problem is by no means unique to ISS, since anti-virus companies have long tended to expand their security offerings by buying appropriate smaller companies.
This matter is particularly noticeable in ISS, due to the number of options having been cut in the components, especially the anti-virus configurations. This gives an impression of a vast, sprawling set of applications, with each only having a very small number of options within it. One hopes that some stream-lining will be possible in future.
These comments aside, there is no real faulting the contents of ISS, barring the instability issues noted with PestPatrol. Printable documentation could be more logically supplied but that is not a dire sin, since operation is, by and large, fairly easy to understand to all but total novices. A total novice, however, can simply accept defaults in all cases and have little need to interact with ISS – very much as would be hoped for by general users.
Test environment: 1.6 GHz Intel Pentium machine with 512 MB RAM, 20 GB dual hard disks, DVD/CD-ROM and 3.5-inch floppy drive running Windows XP Professional SP2. AMD64 3800+ machine with 1 GB RAM, 80 GB hard disk, DVD/CD-ROM and 2 MBit ADSL Internet connection running Windows XP Professional SP2.
Product: eTrust Internet Security Suite 7.1.
Developer: CA Inc., One CA Plaza, Islandia, NY 11749 USA. Tel: +1 631 342 6000; email [email protected], web http://www.ca.com/.