2005-07-01
Abstract
Detailed testing and analysis of Symantec AntiVirus 10
Copyright © 2005 Virus Bulletin
I never know quite what to expect when a new product version number is announced by an anti-virus vendor. On the one hand, a vast number of changes may have been introduced - which can be interesting, yet confusing initially. At the other end of the spectrum are those products in which the new version remains all but identical to the old one, leaving the user (or reviewer) mystified as to exactly where the improvements lie. Where Symantec's new version is positioned in this range should become more obvious as the review unfolds.
The brief thumbnail sketch of the vendor I usually include as part of the introduction to product reviews seems somewhat superfluous in this case. I have vague memories of a Symantec defragmentation application being bundled with some of the earlier versions of Windows. Ironically, back then I wondered whether the company would either be taken over by Microsoft or vanish as its products were assimilated into Windows standard features. It seems I need not have concerned myself. In the battle for the anti-virus vendor number one spot in terms of sales volume, Symantec's position has been in the top two for many years now. Since the number one and two positions are very much dependent upon who is counting and what is counted, a stronger position in the market is not currently achievable.
As far as current product lines are concerned, Symantec's offerings are many and varied. The anti-virus product has expanded, as is common nowadays, to cover a broader range of threats than before, with anti-spyware and anti-adware capabilities and increasing integration with the Symantec firewall products. The company's firewall offerings are part of a range of security and networking applications, including intrusion detection, vulnerability assessment and network status tools. Remote computer control is offered through PC Anywhere and imaging through Ghost. The anti-virus software is offered on a variety of platforms, though on this occasion Windows was used for testing.
At the time of writing this review, the first few boxed versions of Symantec AntiVirus (SAV) 10 were rolling off the production lines. Unfortunately, however, a slight delay in the supply chain between manufacturer and my desk resulted in my having only an electronic version of the software for review. This was supplied as the entire contents of the SAV CDs, however, so all that was missing was the hard copy documentation. Past versions of SAV have been supplied with a 'Getting Started' gatefold card and a comprehensive installation manual, and I would expect much the same with this release.
The documentation in the electronic version is collected in one directory and is mostly in PDF format, with Acrobat Reader supplied for convenience.
There is one text file in the documentation, which is the reference guide for the use of MSI in the installation of SAV. This provides information on commonly-used command line switches and examples of their use. This was also where one of the new features in SAV 10 was first revealed to me (although the changes are described at length within one of the PDFs). With Windows XP Service Pack 2 installed the operating system can complain vociferously if a firewall is not installed locally. In many circumstances a LAN will be running numerous applications which either fulfil firewall functionality at one point, or would be hindered by the default settings of Windows firewall. SAV can be set up so as to suppress these warnings from the Windows Security Center. Other functionality is also available to interact with the Windows Security Center, most aspects of which can be controlled during SAV installation.
The documentation supplied includes PDF versions of both the installation manual and Getting Started card. The manual retains much the same style as the older one. For those unfamiliar with the Symantec documentation, it is one of the more easily used of those supplied by current vendors. The user can select from dedicated manuals for various aspects of functionality. As mentioned, one manual is dedicated to installation, while others cover central quarantines, LiveUpdate control, client software information and, of course, the more general Administrator's Guide. There is also a 50-page reference guide which covers the areas most likely to cause confusion.
With all the documentation available, the online help files should not require too much use, and are present in all those applications tested, with the notable exception of the LiveUpdate Administration utility. Where present, the help function information is comprehensive and is not simply a direct copy of the PDF documentation ported into help format.
With a product so obviously designed for centralised administration, the obvious test scenario was to install it on a server and then see how easy it would be to install to various attached workstations. In order to test this, several components needed to be installed. The first few times that I tested SAV's administration tools the process proved to be very involved, with numerous installs required, in the right order, to obtain a centralised installation. With this release the situation has improved significantly, although it is not totally intuitive yet.
When running the installation application from the CD, the user is presented with the option of installing SAV or installing Administrator Tools. There is also the option to 'Read This First', which is very much advisable. In fact, this consists of links to the most relevant parts of the PDF documentation, and somewhat deep within the information provided through these links is the correct order for installation, this being: 'Install the Symantec System Center. Install Symantec AntiVirus server software on the same computer as the Symantec System Center, and configure it as a primary management server. Install Symantec AntiVirus client software on other computers.' It would have been nice to have had an option available to perform each of these processes in turn.
The components inspected in this review were the Symantec System Center and SAV itself on client and server. In addition, the LiveUpdate Administration (LUA) utility was examined, since this can be used to control updates in a networked installation. The LUA utility seems to be the nearest thing to an afterthought supplied in the package - as mentioned already, it does not have the same level of integrated help available, and it was not noted as a standard part of a SAV installation. In fact, the utility covers all Symantec products which make use of the LiveUpdate mechanism for updating components.
As suggested, the Symantec System Center was the first component to be installed. This requires Internet Explorer version 5.5 or higher to be available on the machine in question. For the purposes of testing, therefore, Windows 2000 Server with Internet Explorer 6 was chosen as the installation environment.
After the usual licence agreement has been accepted, the components to be installed can be selected. This area gives an idea as to the functionality offered within the System Center - Symantec AntiVirus and FireWall snap-ins and the server and client remote installation tools being selected by default. Alert Management System Console is not installed by default, but may be added to the selected packages here. For the purposes of the test all possible options were installed. Once the components have been selected, the installation completes with little further interaction required, although a reboot was required after installation.
Next on the to-do list was the installation of the Symantec AntiVirus Server software on the same machine. This is performed by selecting the action to install the software, rather than deploy it, from the CD setup menu. The choice appears as to whether a server or client installation is required, after which installation settings may be altered. Rather than consisting of major server-specific functionality, the options here are merely whether the GUI, help files and quarantine client files are to be installed. These are all installed by default, with there being few reasons likely to warrant a change from the settings provided.
Server-specific settings do occur in the second phase of configuration choices. Here, the password and username for the machine's Server Group must be selected. A Server Group in this context is a group of machines which can be configured en masse. Such groups are not limited to containing a single server machine, though one server must be designated as the primary server for the group. If the Server Group name chosen is not already in existence a check is provided that this is a new group, rather than a typo, after which general settings for the installation are also chosen. At this stage the general settings are simple: whether to use Auto-Protect, the on-access component, and whether to use LiveUpdate when the installation has terminated. With these choices made installation completes without further ado.
A reboot is not required after this part of the installation chain. Somewhat confusingly this server installation does, however, show up as having installed Symantec Client Security. Admittedly the security is provided for the clients, but seeing this as the result of a server installation led me to believe that I had installed the incorrect software at first.
At this stage the machine in question is ready to be configured as primary management server for the newly created Server Group. This is performed through the Symantec System Center (SSC). SSC is implemented as snap-ins for the Microsoft Management Console (MMC), thus offering a centralised area for configuration changes with any other MMC-integrated applications. Upon launching, this offers what amounts to a direct link to various FAQs - falling under the headings of 'Management Console', 'AntiVirus Protection Management' and 'Firewall Protection Management'. At this stage, however, these are distractions from the task in hand, and the user is better served by selecting the Symantec System Center tree in the left-hand pane. Other functionality will be discussed later in the review.
Selecting the Symantec System Center tree brings up the System Hierarchy tree which, as a default at this stage, consists of just one server group, 'Symantec AntiVirus 1'. What is not immediately obvious is that the red diamond forming part of the System Hierarchy label is a decoration, rather than a sign that all is not well with the SSC settings. There is a problem nonetheless, in that there is no default primary management server. The server group is locked by default - unlocking requires the username and password provided during the installation. The username and password may be saved within MMC in order to automate the unlocking on future occasions.
With the preamble completed the newly-installed server may be edited to become the primary management server. At this stage there is a change in the tree labels for the server itself, where the new labels for the server change from red to blue to indicate that there are no problems.
With the SSC settings tweaked as directed in the installation documentation, it is possible to return to the process of installing clients. The CD setup menu is where this operation is performed. Client machines were running Windows XP, both with and without Service Pack 2, and were located in a domain which included the server machine. At this stage the 'Deploy AntiVirus Client to 2000/XP/2003' option was selected, which launches the ClientRemote Installation application. As the first part of this application the path to the installation files must be supplied. This mentions several places which have not even been hinted at in the process so far, making it a happy event when the default location worked with no further thought required.
With the source location having been supplied, the management server and the destinations must now be selected. ClientRemote Installation detects machines reachable over the network which may be selected for installation via a GUI. All machines on the network were presented here, although if workgroup-based machines or machines without Internet Explorer 5.5 or later were selected, the process of installation was noted as being impossible if attempted.
Having selected the machines towards which to roll out the software the remainder of the process simply involved activating the process and watching the progress bars. Somewhat ominously, the instructions after installation were to check whether machines required a reboot. Among the test machines examined, however, no reboots were required. With the server and clients now in place, all that remains for basic functionality is to ensure that updates occur properly. For machines with a direct Internet connection LiveUpdate is the most obvious update facility provided, though not one that will be very popular in larger or more managed organisations. The LiveUpdate Administration utility is of help here. This enables a customised hosts file to be produced, pointing to a central repository within the organisation. This repository can be attached directly to LiveUpdate, or fed material from the LiveUpdate servers after it has undergone internal testing. The LiveUpdate Administration (LUA) utility, as mentioned before, is somewhat less elegant and less well documented than the other portions of the software, but it works nonetheless.
The Symantec System Center has, if anything, too many features to allow for a full discussion. Luckily the majority of these features exert control of the clients at a distance and a discussion of client functionality will thus cover a large proportion of what the SCC can be used for.
Such conveniences as forcing client updating, applying a degree of randomisation to scheduled client updates and locking down client-side configuration changes are supported of course. The latter has had additional care applied, as spyware has increasingly aimed to sabotage or subvert security software. Communication between client and server is now secured cryptographically, with the ability to configure key durability for the paranoid. Any attacks on SAV are also noted and can be pre-empted and logged, though the latter option is not turned on by default.
The default hierarchy is rather simpler and more monolithic than can be constructed using SCC. Within each server group, for example, can be defined client groups, each with their own set of rules. These client groups can be created arbitrarily based on machine requirement similarity, without reference to where in the network structure they are located logically. The SCC allows for different users to be allowed different levels of control over the settings of SAV.
All of this is much as expected, so we can return to the client software itself - all functions as noted here are also controllable and can be initiated from the SCC. The client is of the standard two-paned type beloved of Windows developers, the left pane containing the trees of View, Scan, Configure, Histories and Look for Help.
The View tree can be used to produce views of on-access file scanning details and the scheduled scans set up for the machine. In addition, the quarantine, backed-up items and repaired items can be viewed here. Obviously some of these areas will be very dull indeed, since it is not guaranteed that any viruses will be discovered. For a general user, however, this may be their only clue as to the presence of any infections on their machine, since the administrator can set disinfection options to be invisible to the user.
The Scanning tree consists of three preset scans: Floppy, Full Scan and Quick Scan. Custom scans may also be set up here. These offer all the usual choices, though the options available are much more technically detailed than would have been the case a few years ago. I suspect that they may still be a little too advanced for the average user - but it is nice to have this level of detail as to what options actually mean when implemented. I, for one, would far rather see more details than some incomprehensible trademarked name which means the same thing when translated.
Perhaps more care than usual is devoted to the treatment of files migrated during backup procedures. This is an area where headaches look possible, though the attention will probably be ignored by most, and praised effusively by those who are directly affected. It is also of note that the default option is now for active scanning for spyware and adware. A different treatment may be set for each of these threats when detected, along with associated jokes, tools and an assortment of other categories. This differentiation is a good thing to see, though perhaps an area where the 'correct' action will be open to debate.
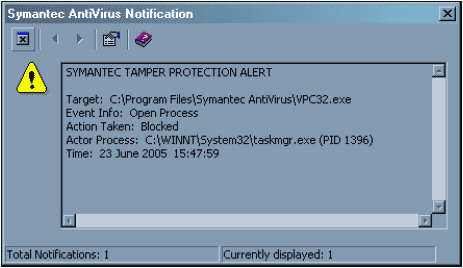
The Configure tree is devoted to the on-access functionality of the software. This is primarily the on-access virus scanning, though the Tamper Protection functionality also falls into this category. This allows alterations to SAV to be either blocked or logged. I did not, however, manage to trigger either function while using the simplest of attack methods: deleting SAV files randomly. However, it did block and notify when attempts were made to halt Symantec-related processes.
The deleting of files did have an unexpected side effect, in that the installation routine was triggered, replacing the affected files. However, this self-repair functionality was limited in the test environment since deleted virus definitions caused the process major problems. This should be less of an issue if LiveUpdate is attached to the Internet whether directly or indirectly.
The last two views, Histories and Help, are self-explanatory, showing the various log files and the online help. In addition to the standard Threat History, Scan History and the Event Log, this is the area where the Tamper History log can be inspected.
Rather than being a significantly different product from its previous incarnations, SAV 10 is very much SAV 9 with additions. These additions are relatively small in number and reflect, by and large, the need for greater internal security within SAV's infrastructure and the integrity of its operation.
Some might point out that the small number of changes involved are as a result of Symantec having put every possible feature into the software already - the client installations here came to 115 MB, while the server installations were a substantial 225 MB. There certainly seemed to be little lacking in the tasks I set out to perform. This completeness is aided by the documentation supplied, which is large in both quantity and quality.
The major perceived weakness of the product still lies in the installation procedures, which remain far less simple than could be the case. Admittedly, when rolling out software to a large network this could be a good thing, since having to 'look before you leap' is likely to help some decisions to be made more carefully. Overall, however, the process could be more automated - a fact which is even more obvious when reading through the SAV documentation on this very subject. On the other hand, the situation is a lot clearer and less prone to problems than in the past.
SAV 10, therefore, can be seen as an evolved version of SAV 9. It will shock few and be easily usable by current SAV administrators. The changes within it reflect current malware trends, which cannot be a bad thing. With more proposed integration of security into Windows itself on the way in Longhorn, however, I have my suspicions that SAV 11 will include a far greater set of changes than we have seen in SAV 10.
Test environment. Identical 1.6 GHz Intel Pentium machines with 512 MB RAM, 20 GB dual hard disks, DVD/CD-ROM and 3.5-inch floppy drive running Windows XP Professional, Windows XP Professional SP2 and Windows 2000 Server SP6.
Developer. Symantec Corporation, 20330 Stevens Creek Boulevard, Cupertino, CA 95014, USA; tel: +1 408 517 8000; email: <[email protected]>; website: http://symantec.com/.