2010-01-01
Abstract
2009 was filled with security stories involving spam, malware and cybercrime in general. Terry Zink takes a look back at the ten biggest newsmakers.
Copyright © 2010 Virus Bulletin
2009 was a year filled with security stories involving spam, malware and cybercrime in general. It was a jam-packed year, so let’s take a look at the ten biggest newsmakers.
Conficker is a piece of malware that first appeared in late 2008, but its story didn’t really heat up until 2009. The story is noteworthy not because of the impact of Conficker, which in itself was large; instead, the story is important because of the way in which the industry responded to the problem.
Conficker is a worm that uses flaws in the Windows operating system to add its hosts to a botnet and execute remote instructions. A patch was released for the Windows vulnerability in October 2008, but Conficker appeared in November 2008 and began to exploit the vulnerability. The worm used a number of advanced techniques and became the most prevalent piece of malware detected in 2009. Conficker is thought to have been named by rearranging the letters of trafficconverter.biz, which was a site used by early versions of the worm to download updates:

In spite of the advanced techniques used by Conficker, security researchers managed to discover an update mechanism through which infected computers could download additional instructions. The researchers reverse engineered an algorithm that would generate 500 new domain names per day, which the malware would then use to connect to its command and control centres. The researchers began a process of manually registering each of the domain names in advance, so that any attempt by Conficker to contact them would fail. However, it soon became clear that registering so many domain names would be a very expensive undertaking.
Thus was born the Conficker Working Group (CWG). In January 2009, representatives from various security companies, along with the anti-botnet Shadowserver Foundation, got together and designed a strategy to counteract Conficker. One month later, the group had a plan to register as many domains as possible and assign them to a sinkhole – a server designed to capture and analyse malware traffic. ISPs were able to use this data to analyse traffic in order to identify infected systems. At about the same time, ICANN (the Internet Corporation for Assigned Names and Numbers, the group responsible for managing the globe’s IP addresses and Domain Name System (DNS)) invited representatives from the group to present their findings to the ICANN board and expressed that it would help where it could. The Conficker authors still managed to register some domains, but members of the CWG had computed a year’s worth of Conficker domains in order to direct them to the sinkholes. It looked like Conficker may be thwarted.
However, in March a new Conficker variant appeared: Conficker.D was scheduled to register as many as 50,000 new domain names per day across more than 100 top-level domains (TLDs), starting on 1 April 2009. This looked like too big a task to tackle, but the CWG managed it. They secured the cooperation of all of the owners of the TLDs to register or block the new domains in question. April 1 came and went, but by that point the domains had already been blocked.
The fight against Conficker is not yet over. Estimates of the number of computers infected by Conficker are in the region of five to ten million. And once in a while, legitimate domains collide with Conficker domains and are blocked. New variants of Conficker may yet be released, and no one really knows for sure what Conficker’s purpose is, other than perhaps acting as a conduit to serve other botnets. However, the rapid, effective response by industry to the threat that this malware posed serves as an example of what can be accomplished when interested parties work together. It is possible to stop malware from spiralling out of control.
In August, users of the Twitter social-networking site discovered that their favourite 140-character messaging service was offline. ‘What’s going on?’ they asked. ‘People need to know what I had for breakfast!’
It turned out that a co-ordinated Distributed Denial of Service (DDoS) attack had been launched against a number of social networking sites including Twitter, Facebook, LiveJournal, YouTube and Blogger. But whereas the other sites were able to repel the attacks, Twitter was not.
On further analysis the disruption appeared to be the result of a targeted attack against one particular blogger by the name of Cyxymu (Sukhumi), which is the capital of the Georgian breakaway region of Abkhazia. Cyxymu had accounts on each of the aforementioned services and posted messages on the topic of civilian suffering during the war – he was decidedly anti-Russian. In August, a large spam run containing links to Cyxymu’s various social networking pages coincided with the DDoS attacks on the sites. It resembled an attempt to make it look as if Cyxymu had sent out a huge spam run to drive visitors to his pages to support his cause, and that his campaign had backfired when all of the new traffic shut down the sites, and then backfired again when Facebook, Twitter, et al. all found out he was spamming to get people to come to his pages. Perhaps the attackers thought that this unethical behaviour (spamming) would get him suspended. It almost sounds like the plot of a Hollywood movie.
In reality, while Twitter did go offline for a time, the other sites did not. In fact, they became adamant that they would not shut down Cyxymu as he was entitled to his rights to free speech. Cyxymu, so it is thought, was innocent and was the target of a cyber attack in an attempt to silence him. In the United States, an attempt to shut somebody down for exercising their rights to free speech is almost always met with contempt.
This was not the first time that politics had been mixed with cyber riots. In 2007, the Estonian government was hit with cyber attacks that shut down its infrastructure after it had attempted to remove a Russian World War II monument from downtown Talinn. In 2008, during the Russian/Georgian war, DDoS attacks took Georgian and Azerbaijani sites offline.
In the 21st century, politics and cyber attacks have become increasingly intertwined. And August’s Twitter attack wouldn’t mark the last time that hacktivism would make a splash on the political scene in 2009.
One of the top stories of 2008 was when Californian ISP McColo was taken offline after a story was published in The Washington Post describing how it acted as a command-and-control centre for botnets that send spam and host fast-flux or server malware. Almost immediately after the shutdown, global spam levels plummeted. This showed that, given enough motivation, there was a mechanism to fight back against spam if the spotlight was shone on the public sector.
2009 also saw its share of ISPs taken offline. In June, the US Federal Trade Commission filed a motion of complaint to have Pricewert LLC, an American ISP, taken down. In August, Latvian ISP Real Host, which was responsible for numerous botnet command-and-control centres, was similarly disconnected. But the major talking point of these two disablements was not how much spam volumes decreased, but how little impact there was on the global spam volume.
Pricewert’s removal saw spam levels drop slightly – less than 10% – but within days everything had returned to normal. The takedown of the Latvian ISP registered no discernable change in spam levels at all. Indeed, what we learn from the Real Host outage is that spammers learned from the McColo outage: they no longer place all of their eggs in one basket. They have adapted and evolved so that they are no longer solely reliant on a single point of failure, and seem now to be building some redundancy into their networks. The short-lived elation of seeing McColo taken down has worn off and we are left with the grim reality that spammers are coming back more resilient than before.
In November, the small security company FireEye was able to disable a botnet that at one point was responsible for perhaps a third of the world’s spam. Security researchers from the company analysed the workings of the huge botnet known as Mega-D (or Ozdok) and managed to infiltrate its command-and-control structure. They were able to send a new set of instructions to all of the zombie hoards that make up the Mega-D botnet. After doing this, spam from Mega-D slowed to a crawl. FireEye had succeeded.
What is extraordinary about this is that a relatively small company was able to take down a very large spam operation that has a vested interest in keeping its infrastructure up and running. Mega-D had built in redundancy to guard against this very thing by reserving a long list of domain names for its command-and-control centres, as well as using hard-coded DNS servers. It also had software to dynamically generate new domain names on the fly [1].
It remains to be seen whether Mega-D will remain offline for long. As we saw with Pricewert and Real Host, their takedown had merely short-term effects on the spam problem. When the anti-spam community comes up with a technique to disable the spamming infrastructure, spammers react by building a better one. The battle continues.
As Americans celebrated the 4th of July weekend with backyard barbecues and fireworks, various government employees had to put their hamburgers and potato salads to one side.
That weekend, a large-scale DDoS attack hit the Federal Trade Commission, the US Department of Transportation and the US Treasury. The US Secret Service, Department of Homeland Security and the State Department were also hit. So were several government websites in South Korea. The attacks were particularly severe, taking up 40GB of data per second – much larger than a typical attack.
As the attacks began to wane [2], various trojans that had infected the PCs used in the attacks started to overwrite data in the hard drives with a message that read ‘memories of independence day’, attempting to write over every physical drive of the compromised systems. Thus, the trojans had a self-destruct feature that was designed to inflict maximal damage.
So who was behind these attacks? Shortly after they occurred, South Korean officials blamed North Korea, or at the very least, pro-Pyongyang forces. North Korea, of course, denied involvement. What clouds the issue is that the attacks need not have been government sponsored. They could equally have been the work of pranksters or industrial spies. Were the North Koreans responsible for the attacks? Maybe they were, maybe they weren’t. Certainly, the IPs used in the attacks were located in the Far East, but that doesn’t mean that the people responsible for controlling them were.
What is more worrying is the fact that the DDoS attacks actually succeeded in disabling the government websites. These types of attacks are things that private ISPs see every day and repel every day. Yet, the governments had a single attack against them and just like that, their sites were taken down. This illustrates the current vulnerability of governments in the cyber arena – they can’t defend against the sort of attacks that industry has been handling for years.
Perhaps the US and South Korean governments need to join up with Twitter and form a support group.
2009 saw some pretty heavy hitting in the legal arena in the spam world. In June, ‘spam king’ Alan Ralsky pleaded guilty to a stock fraud case where he pumped up Chinese penny stocks.
In 2004 and 2005, Ralsky, along with a small group of other people, conspired to manipulate stocks using spam messages to ‘pump-and-dump’ their value. In other words, they would pick a stock, buy shares in it, send out a huge number of spam messages claiming that the stock was poised to go through the roof, and then wait for the rest of the world to buy it in droves. This buying surge would send the price up, at which point Ralsky and his group would sell their shares and collect the profit. Once the buying surge was over, the stocks would return to their previous value. The stocks were typically low-priced ‘pink-sheet’ stocks for US companies owned by people in Hong Kong and China.
Ralsky used all sorts of spamming techniques to get his message across, including the falsification of email headers and extensive use of botnets.
Ralsky was one of the world’s most prolific spammers. He reportedly once admitted to sending more than 70 million spam messages per day. At 70 million per day, even a hit rate of 0.01% equates to 7,000 actions being taken. Eventually, though, his crimes caught up with him and he pleaded guilty to wire fraud, mail fraud, money laundering and violating the United States’ CAN-SPAM Act. In exchange for lighter sentencing, he agreed to provide assistance in the prosecution of other spammers.
Yet Ralsky did not get off lightly. In November 2009, he was fined $250,000 and sentenced to four years in jail. However, many anti-spam advocates doubt that this is enough.
Across the ocean, another spammer was also hit with a huge fine. In November, the US Federal Trade Commission (FTC) fined Lance Atkinson $15 million. Atkinson is believed to have been behind the spam affiliate Affking, the folks who brought you such delights as the Canadian Pharmacy’s cheap drugs and Herbal King’s wonderful line of weight loss pills.
Atkinson is a New Zealander now living in Queensland, Australia. If the FTC is able to collect, it will be a significant victory against spammers. While spammers do make a substantial amount of money from their illegal activities, $15 million is an extremely large amount to be taken out of their coffers. Spamming is about the money, and huge fines like these are a deterrent – if the spammer gets caught. The FTC was fortunate in this case because Herbal King flagrantly violated the CAN-SPAM Act by faking headers and not providing valid unsubscribe links. Next time they may not be so lucky.
Even Facebook got into the game this year. In October, a judge in San Jose, CA, awarded Facebook a $711 million judgment against alleged spammer Sanford Wallace. Filed in February, the suit alleged that Wallace sent misleading messages to Facebook users with malicious links, tricking them into giving up their credentials. In addition to the fines, Wallace and his gang face possible prison time for their actions. Wallace declared bankruptcy in an attempt to avoid payment of the various suits he has been saddled with (and lost).
So, while in general spammers get away with what they are doing, sometimes it does catch up with them. And we, in the anti-spam and e-security community, can enjoy a little bit of schadenfreude, if only for a little while.
One of the biggest trends in spam over the past two years has been black search engine optimization, or black SEO. 2009 was not the year it started, but it certainly was the year in which it really accelerated.
Black SEO comes in two main flavours:
Malvertising. When you perform a search on Bing, Google or Yahoo!, you will often see sponsored search results on the side of the screen. In legitimate cases, sponsors pay for their ads to be displayed on the side, in the hopes that the user will click on them and be directed to their websites. This is the advertising model that provides so much income for Google, Microsoft and Yahoo!.
However, spammers and distributors of malware have exploited this facility by also purchasing ad space; when a user performs a search and clicks on the sponsored result, the page is not a legitimate web page but instead is a link to malware. The user has been lulled into a false sense of security, assuming that all paid-for advertisements are legitimate – after all, who would pay to advertise malware? Doesn’t it destroy the attacker’s cost model? The answer is no, it doesn’t, and malvertising is something that strikes at the very heart of Google, Microsoft and Yahoo!’s revenue model.
Page rank optimization. This is similar to malvertising, but in this case the attacker doesn’t need to buy advertising space in order to infect a user’s computer. Instead, all he needs to do is make sure that his page is near the top of the search ranking.
To accomplish this, a spammer will create a malicious page containing links to malware, or perhaps their spammy product, or perhaps a phishing page. They will then utilize a variety of techniques to make sure that users see their page. One such technique is to look for what the current most popular search term is, such as ‘Jessica Biel’ (thank goodness we have finally moved on from Britney Spears and Paris Hilton). They will then tag their web pages with ‘Jessica Biel’ meta-tags. At the same time, they will send out armies of botnets to plague discussion forums and blog comment forums with pointers to these web pages. With so many web pages and pingbacks pointing to their malicious page, the trap is set.
Google, Bing and Yahoo!’s web crawlers crawl the Internet, indexing popular pages. Because spammers know that Jessica Biel is a popular search target, and because so many pointers on everyone else’s pages now point to their spammy landing pages, the landing pages end up near the top of an Internet search. The result? Somebody legitimately searching for Jessica Biel will see the spammer’s page near the top of an Internet search. They click on the link and voilà – free traffic is driven to the malicious site.
Black SEO in each flavour destroys the confidence of the end-user and, among spammers, is the growth industry of 2009.
Reputation hijacking continues unabated in the world of spam and malware, and social engineering is the tactic of choice.
Social engineering is the process by which an attacker will prey on a person’s emotions in an attempt to get them to do something that they otherwise might not do. Two of the primary emotions that are targeted are the same as those that drive the stock market: fear and greed.
The general public has a vague notion that they need to run security software in order to keep their systems clean. They understand that there are computer viruses out in the wild that mean to do their computers harm; they have a genuine concern. Malware writers understand this. They know that people want to avoid getting infected, so now they provide a solution – cheap, or sometimes even free, anti-virus software!
To accomplish this, a well-known piece of software such as Microsoft’s Windows Security Center will be spoofed (see Figure 4). The user, recognizing Microsoft’s splash page reminding them that they have no anti-virus protection, can’t resist the lure of cheap or free software to protect them from the nefarious world out there. They are also fearful of becoming the next virus victim and want to prevent this. Not necessarily thinking things through (when our emotions interfere with the logical parts of our brains they usually win), they download the advertised cheap or free software and install it. Unbeknownst to the user, their system is infected and more vulnerable than ever.
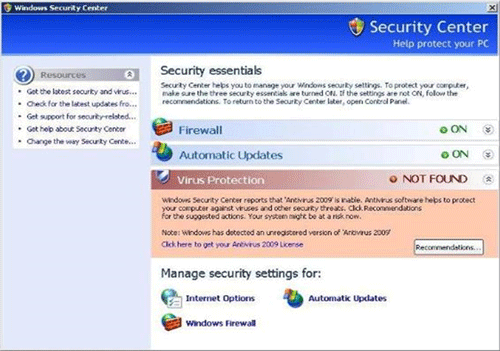
Figure 4. Screenshot of FakeXPA, the sixth most prevalent piece of malware detected by Microsoft in the first half of 2009.
The story of rogue anti-virus software is not new to 2009. It has been going on for a while. What makes the rogue anti-virus story newsworthy for 2009 is that it is still a big problem and is getting worse.
Long criticized for its insecure software, or rather the perception of insecure software, Microsoft made a splash into the home-user market in 2009 when it released Microsoft Security Essentials [3], a free anti-virus program for registered users of Windows.
Microsoft has already made significant inroads into keeping software secure:
The Malicious Software Removal Tool [4] is a free tool for scanning and removing unwanted and malicious software for registered and unregistered copies of Windows.
Microsoft Update is an automated process for downloading critical updates to keep your software secure. The more up to date you keep your system, the less likely it is to be exploited.
In 2002, Microsoft launched its Trustworthy Computing [5] initiative to improve public trust in its own commercial software. In addition, the company participates in a number of industry collaborative groups such as the Anti-Phishing Working Group (APWG), the Messaging Anti-Abuse Working Group (MAAWG) and the National Cyber Security Alliance (NCSA).
Microsoft’s Software Development Lifecycle requires that all of its products go through the Secure Windows Initiative, a process where potential security risks are identified and mitigated.
What makes the new home-user anti-malware product different is that it is free; the company now offers consumers anti-spam and anti-malware services, putting it on a par with other traditional security vendors such as McAfee and Symantec, and joining the ranks of free anti‑virus providers including AVG, Avira, Alwil, PC Tools and others.
There’s now no reason for a licensed user not to run anti-virus software. There are many choices out there, and Microsoft recommends you run something. So does the anti-spam and anti-malware community.
In October, an unusual article was posted on the technology blog Neowin – it was a large posting containing approximately 10,000 usernames and passwords belonging to Hotmail users. Many theories floated about. Whose usernames were these? What were they used for? How did the hacker gain access to them? Is my username and password at risk? Are these victims of a phishing scam? Did they get past Hotmail’s spam filter? The problem was complicated further by the fact that Yahoo! Mail and Gmail (Google Mail in Europe) accounts were also compromised, with various account details from those services also posted [6].
Regardless of how the hacker gained access to the accounts, what became painfully clear was that users in general do not follow good security practices. The most common password was ‘123456’. The second most common password was ‘123456789’. Armed with information like this, an attacker wouldn’t necessarily need to know someone’s password to break into their account. All they would need would be a lot of usernames and then they could try those two passwords and see which ones turned the key in the lock. Given enough usernames and passwords, some of them will undoubtedly unlock the doors that seal shut financial records. Who needs lock picks (other than magicians and locksmiths)?
While some hacker somewhere broke into a bunch of people’s email accounts, in December, another news story broke. One of the hottest stories of the past decade is that of global warming. On the one hand, groups of scientists have published mountains of evidence indicating that the earth’s global and atmospheric temperature is increasing and that this will change weather patterns, which will lead to decreased living standards in most of the world and negatively impact the prosperity of humanity. The scientists believe that this change in the world’s climate is primarily the result of human activity.
Meanwhile, sceptics claim either that the evidence for global warming is overstated, or that its potential impacts are exaggerated, that the links between human activity and global warming have a weak or unknown correlation, or that the economic costs of preventing climate change outweigh the benefits of attempting to reverse it.
As the world prepared for its leaders to converge in Copenhagen to discuss potential solutions to the problem, a story broke. A hacker had broken into a server used by the Climatic Research Unit (CRU) at the University of East Anglia in Norwich, England. The hacker stole and disseminated over a thousand emails and other documents that had been compiled over the course of 13 years. The website RealClimate was then hacked and portions of the emails were uploaded to the site. What was particularly damaging, depending on how you look at it, was the way in which the emails could be interpreted. The sceptics claimed that the emails and documents were proof of a massive conspiracy to hide or manipulate data in order to support their case for global warming. One excerpt, written by Kevin Trenberth, a climatologist at the National Center for Atmospheric Research, discussed gaps in the understanding of recent temperature variations: ‘The fact is that we can’t account for the lack of warming at the moment and it is a travesty that we can’t.’ [7]
Of course, there are different ways to interpret the emails. Trenberth told the Associated Press that the phrase was actually used in reference to an article he authored calling for improvement in the measuring of global warming to describe unusual data, such as rising sea surface temperatures. The word ‘travesty’ refers to what Trenberth sees as an inadequate observation system.
The fallout from all of this is entirely political; the emails can be interpreted in different ways by different people. Once again, the politics is driving cyber attacks in an attempt to get people to support a certain set of beliefs. We need to be careful what we say and do because somebody with an army of botnets, or a certain set of computer skills, might not be on our side and might have the mechanism to do us a great deal of harm.
Well, that’s the way I saw the security world this year. There were other notable stories that didn’t make my cut: Canada finally got around to passing an anti-spam bill (almost), ICANN is set to release a bunch more top-level domains, and URL-shortening services were abused in droves. But I think the stories above are the ones that made the greatest impact on the world in general.
As we enter the new year, I look forward to seeing what stories unravel in 2010.
[5] See http://www.microsoft.com/mscorp/twc/default.mspx for more details on this initiative.
[6] See Virus Bulletin, December 2009, p.12. http://www.virusbtn.com/virusbulletin/archive/2009/12/vb200912-Hotmail-Yahoo-Gmail-hack.