2009-03-01
Abstract
Rising is one of China’s most venerable security firms, having produced its first anti-virus products as long ago as 1991. As the company begins to build a presence outside its home territory, John Hawes takes a detailed look at flagship product Rising Internet Security.
Copyright © 2009 Virus Bulletin
With China’s economy becoming ever more dominant on the world stage, and with swathe upon swathe of a massive populace moving up the socio-economic ladder and getting online, it is no surprise that the country’s software industry is booming – and, of course, security is a significant area of that market.
Rising is one of China’s most venerable security firms, having produced its first anti-virus products as long ago as 1991. The company has operated under its current identity (full title Beijing Rising International Software Co. Ltd) since 1998, and in recent years has begun to build a noticeable presence outside its home territory. Clients listed on the firm’s website include an impressive array of Chinese government bodies, utility providers, financial and academic institutions, but also some major corporations in Japan, Germany and elsewhere.
Joining the VB100 tests in 2007, after a few false starts Rising’s products have built up a solid string of results, with passes in each of the last three tests entered, and have impressed with solid stability and slick design. The company’s latest flagship product, Rising Internet Security 2009, is joined in the line-up by standalone anti-virus and firewall, and a selection of free products including the now ubiquitous online scanner.
Rising’s international presence on the web is at http://rising-global.com, where the tagline is ‘Lion-strong security’. The company’s emblem, the head of a lion on a golden shield, has become familiar of late to many in the industry thanks to a concerted campaign of handing out trinkets decorated with the lion at conferences, trade shows and other events – the recent VB conference left our office adorned with numerous fluffy lion pen pots and even a few shiny red cushions featuring the lion’s face. As we have learnt from recent comparative reviews, this mascot crops up again in the product. A cartoon version features heavily in a Flash animation which currently dominates the home page of the company’s website – part of a colourful launch campaign for the 2009 product, which offers a 30-day free trial for download.
The remainder of the home page is a little more sober, with a thermometer-style ‘virus alarm’ monitoring outbreak levels (the thermometer having read ‘alert’ over the last few days of checking – perhaps thanks to the ongoing spread of the Conficker/Downadup worm [see p.7]). Further down the page are some company and malware-related news links, a special offer of a one-year, three-user licence for the new product for a pretty reasonable 50 USD, and a section entitled ‘Awards and Certifications’, where the company’s three VB100 awards are proudly displayed, along with a slew of Checkmark certifications from WestCoast Labs.
Elsewhere on the site, alongside the usual information on the product range and sales and download areas, are a more detailed selection of news items and prevalence reports, a partner section and the all-important support sub-site. This includes documentation and a knowledgebase for self-service support. The knowledgebase is reasonably well stocked and the manuals are comprehensive and simply and clearly laid out – although unfortunately, both suffer from occasional inelegancies of translation. The PDF manuals are also rather large and seemed somewhat slow to download and render.
The support section provides an online request system, which appears to be open to all – a registration procedure must be followed before a query can be submitted, but no details of product licensing are required to complete this process. A query submitted regarding a fairly obscure issue noticed during testing elicited a very friendly and fairly helpful response within a few hours. Telephone support does not appear to be an option, at least not outside of China.
When running comparative reviews, getting hold of products from the Far East can sometimes be problematic, with lengthy download times and flaky connections a common source of frustration. Accessing the free trial download of the Rising suite was surprisingly painless however, with the 80MB file coming through on first attempt in around 15 minutes from the default link. Rather sensibly, links to several other download sites, including Tucows and CNet, are also provided.
Setup of the product is fairly straightforward, following through the standard array of steps of approving EULAs, applying licences and so on. A reboot is required after the initial install, and then a series of further setup steps must be followed, including the option to take part in a ‘cloud’ scheme to share suspect samples and scan results with the developers, applying a password to protect settings, informing the firewall of trusted and external networks and interfaces, some further registration and the setting up of scheduled updating.
Finally, the product’s main interface is presented, and with it the cartoon lion, cavorting wildly in the corner of the screen. This mascot, dubbed the Rising ‘Assistant’, appears to have little function other than to entertain with a wide variety of activities, props and costumes, but deactivating him is a simple task.

The interface proper is a slick and attractive affair, with smooth lines and cool colours, and is laid out in a sensible and logical manner. The home page is filled with useful statistics and graphs, accompanied by handy shortcuts to various scans and controls. More detailed information and settings are available on a series of tabs arranged along the top. In most areas, yet more configuration can be accessed from a link to the in-depth configuration window, which opens separately. Explanations and assistance are generally concise and easily available, and even the in-depth tab is reasonably clear (although inevitably it will lose the attention of less learned users once the complexities of the firewall rules are accessed). For those who do not wish to explore further, the default settings seem thorough and sensible.
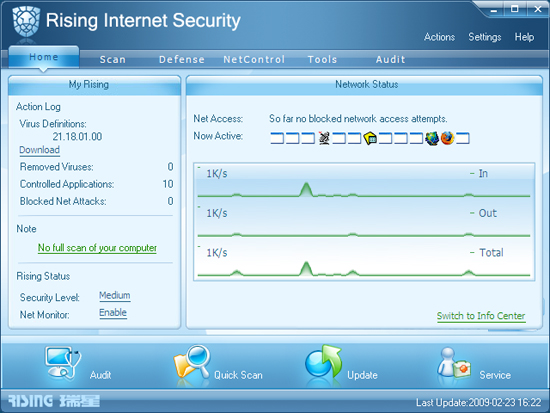
The use of an administrator password is well implemented, ensuring that only trusted users can deactivate or change vital monitors, while allowing the merely curious to perform less dangerous activities. If a password is not applied, the core functions are further protected by a CAPTCHA system, preventing the automated shutdowns attempted by much modern malware. This seems like a sensible self-protection measure.
There are a few oddities in the interface, most of which are attributable to the company’s ongoing process of globalization. A link on the main page marked ‘download’, which refers to an anti-spyware module that does not come installed as part of the main product, leads to a Chinese web page presumably serving the module. Sadly, my Chinese character recognition skills were not up to the task of deciphering the text any further than spotting a large download button – but the site having an unrecognized URL and no obvious Rising branding made me wary of continuing, and many cautious users would likely respond in a similar manner.
Naturally, protection functions form the bulk of the product’s offerings. At the most basic level, and offered on the first available tab, is the on-demand scanner, which is clearly and simply laid out with all the standard functions easily accessible. The main scanner window offers a very clear system for scanning various areas including memory, boot sectors and others, as well as simple on-disk scanning. All are enabled by default. A secondary shortcuts tab offers options to check a number of other areas such as removable drives and the My Documents folder. Basic configuration is provided right there on the main tab, with more detailed tweaks also accessible. Scanning seemed pretty swift and solid – full detection and speed measurements will be available in next month’s VB100 comparative on the Windows XP platform, where relative performance against a wide range of competitors will be measured.
The ‘Defense’ tab provides the bulk of the real-time monitoring, with the standard on-access scanning under the ‘Auto-Protect’ label. This tab is fairly bare, with a button available to disable protection and another providing access to the more detailed settings in the configuration window. Email monitoring is also controlled from here, with SMTP and POP traffic monitored for malware. Although accurate measurement of speed is difficult in such scanners, downloading of mails did seem somewhat more sluggish than normal, but not disturbingly so.
The Defense tab has two other areas. The main one, marked ‘ActiveDefense’, provides HIPS-type detection of suspicious behaviours. This is divided into multiple subsections, with further subdivision in the detailed configuration page. Some of the titles of these are less than obvious at first, with the likes of ‘System Reinforcement’, ‘Malicious Behaviour Interceptor’ and ‘Web Trojan Defense’ not giving away a great deal about the exact type of protection provided by each function. However, more information is provided on perusing the detailed controls. ‘System Reinforcement’, it appears, refers to the standard HIPS functionality, with control available for the selection of areas being guarded, including the registry, core files and processes, and watching for potentially dangerous activities in vital areas. The ‘Malicious Behaviour Interceptor’ applies heuristic rules to watch for further signs of malicious intent, and is configurable only in terms of the strength of the heuristics applied, while the ‘Trojan Defense’ is even vaguer in its purpose, apparently offering yet more behavioural scanning and heuristics, along with shellcode monitoring.
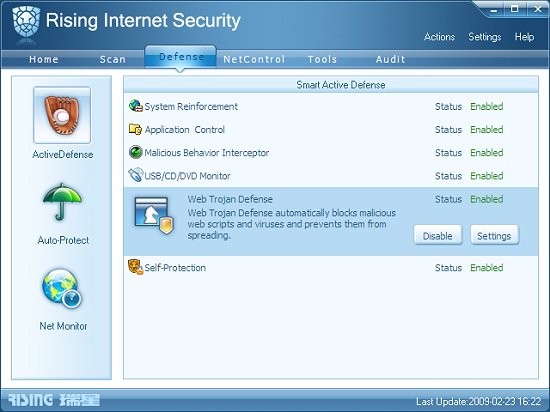
The remainder of the section is a little more self-evident. ‘Application Control’ allows specific programs to be controlled, allowing or blocking specific activities, although the process of setting up such rules is a little awkward, and may be off-putting for the average user. The flip side of this is a whitelist, which can be set up from the detailed configuration tab. Here, selected software can be excluded from the active monitoring. ‘Self-Protection’ prevents unauthorized shutdown or alteration of the protection provided by the product, and the remaining defence covers removable data storage devices including USB, network and disk drives, blocking mounting or execution of programs as required with a reasonable level of granularity.
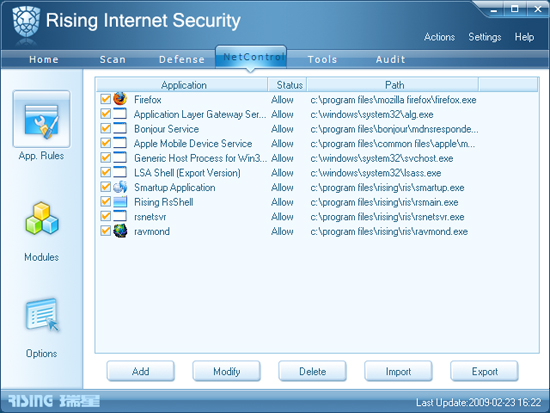
Returning to the top level of defences, the ‘Net Monitor’ provides a similarly in-depth selection of monitors keeping an eye on a range of dangers posed by active network connections and the wild, wild web. This area has a slightly confusing overlap with the previous one, including application control functions, as well as the following area, the more standard firewall setup. The overlap is particularly evident when following the settings link from one of the Net Monitor sections, which leads to the firewall area (the ‘NetControl’ tab). Between them, the two areas provide a thorough range of controls over both inbound and outbound traffic, including cloud-based real-time black- and whitelists of malicious and trusted URLs, an intrusion prevention system watching for attempts to exploit a selection of known vulnerabilities, and a sensor which detects attempts by any malware on the system to take part in a DOS attack.
The setup reflects a general trend in such suite products, with the traditional scanner approach remaining central, albeit enhanced by developments in heuristic and generic detection, and with additional protection capabilities in the form of HIPS and a firewall interlinked in a series of monitors and controls. The presentation of the controls and their configuration is fairly rational, but as in many cases the complexity of fine-tuning such things is difficult to reconcile with the needs of the average consumer. A reasonable balance seems to have been struck between clarity and granularity, with the default settings and a few minor tweaks likely to be perfectly adequate for most users, while a good degree of personalization is available for those with more demanding requirements and the understanding to implement such tuning.
With such a large number of additional levels of protection on offer, it was difficult to more than skim the surface of their performance, but a selection of samples that went undetected by the traditional scanner were introduced to the system via various vectors and executed where applicable. The majority were easily spotted and blocked at least in part, although at times it was less than clear exactly which of the numerous blockers and monitors had come into play. Some of the malicious samples were allowed to run partially, but attempts to change the registry, initiate network connections, inject code into running processes, or create files such as autorun.inf starter files, were blocked. On a few occasions with these autorun worms, the actual infected file was written to a drive and left there. The file was inactive because the starter file was absent, but it remained a danger; an executable using the folder icon and named ‘New Folder.exe’ could easily be run manually by an inattentive user thanks to the rather bizarre default behaviour of Windows to hide extensions. On occasion, valid activities were also queried, although the default response was to allow after a pause.
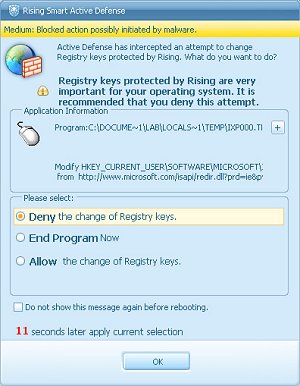
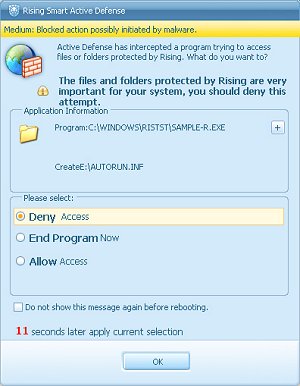
In general, the various active components of the product provide a useful extra layer of defence beyond the standard signatures and heuristics, but they should by no means be regarded as a panacea. We are currently developing a new set of tests here at VB, which will more rigorously exercise such technologies. We aim to begin such tests later this year – hopefully this will allow us to provide a full technical appraisal of Rising’s provisions in these areas.
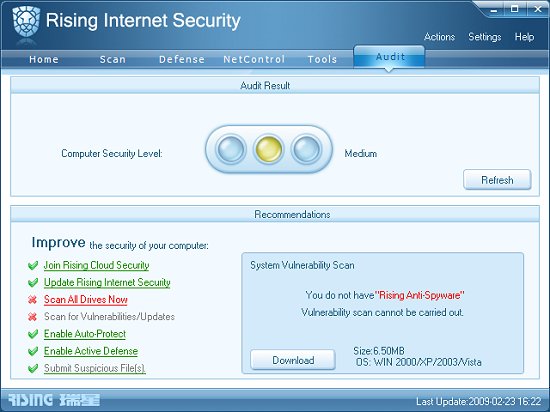
For an added sense of security, an ‘Audit’ tab is provided. This gives a detailed rundown of the status of various protection levels, and recommendations for improvement, with a nice, big traffic-light-style measure to show at a glance how things are going.
A final tab on the interface is intriguingly labelled ‘Tools’, and contains a pretty lengthy list of additional items. Top of the list is the additional anti-spyware component, which is not included as a standard part of the product. Attempting to install this brings up the Chinese web page visited previously from the home tab. This will doubtless be supplemented by multilingual versions as the company’s globalization process continues. Several other product-related offerings are also here, including a registration tool and some controls for the dancing lion ‘assistant’.
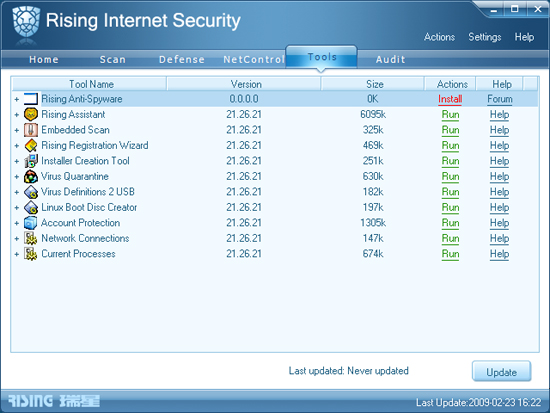
Another tool allows for the creation of a simple installer which will reinstall the latest version of the product at any time – very handy if, say, a machine is being stripped off and rebuilt, as it allows protection to be put in place before any Internet connection is initiated. There is also a utility to create a bootable Linux USB, with the product and latest updates included, for system rescue purposes – an excellent and increasingly handy tool in these days of high-stealth malware.
A few final items include process and network connection monitors, which provide lists of running programs and software connected to the network. The former provide a detailed range of options including killing unwanted processes and access to folders containing the original files for further investigation. The network version has less interactivity, providing little more than a list, but again both are likely to be fairly useful – to the more knowledgeable user at least – and are presented with elegant simplicity.
The final section of note is a tool labelled ‘Account Protection’. This opens a new window, detailing a vast range of banks, games and gaming systems, and messaging software. Download links are provided for each which, in some cases, open the web pages of software providers – generally the Chinese versions – while others simply lead to the online presence of specific banks or payments systems. Not enough time was available to investigate this tool and its capabilities further, but much of its content, for the present at least, seems dedicated to Chinese-speaking users, and indeed users of Chinese institutions. Like some of the other areas of the product, a little more work seems needed to make it fully usable by a worldwide customer base.
Overall, Rising’s suite seems like a pretty well-stocked package. The number of additional items listed in the marketing material, and the interface itself, is perhaps a slight exaggeration thanks to some overlap in functionality, but the pivotal protection elements of traditional anti-malware, HIPS and firewall are all in place, and in the main are implemented pretty solidly. Surface testing did show a few gaps in the protection, but perhaps that just goes to show that no solution, no matter how multilayered, can provide complete defence against a user determined to infect his machine with malware.
Among the swarm of modules were a few items notable by their absence. Parental controls and spam filtering stand out as two such missing features, both having been adopted by most other suite developers of late. However, pretty much all the other bases are covered, in a clean, stable product with very reasonable system impact and one of the most visually appealing interfaces I have seen. Configuration achieves a reasonable balance between accessibility for the novice and granularity for the pro, with few options missing and a much deeper level of system protection possible for those with the training and experience to mould the solution to the specific requirements of their machine and usage patterns.
More details on the detection capability of the traditional scanner, and the speed and system overheads, will be available in a month’s time in the next VB100 comparative, which looks likely to provide details of a very wide range of competitive products for comparison. The most interesting facet of Rising’s product is, of course, the more active protection, for which we continue to work on providing suitable scientific testing. Watch this space for news on these plans later in the year.
Rising Internet Security 2009 was variously tested on:
Intel Pentium 4 1.6 GHz, 512 MB RAM, running Microsoft Windows XP Professional SP3.
AMD Athlon64 3800+ dual core, 1 GB RAM, running Microsoft Windows XP Professional SP3.
Intel Atom 1.6 GHz netbook, 256 MB RAM, running Microsoft Windows XP Professional SP3.