Posted by Virus Bulletin on Feb 26, 2015
As emails were sent to wrong servers, DNSSEC might be worth looking into.
Although, after some initial hesitation, Lenovo was rather frank in its admission of messing up regarding the Superfish adware, it was too late for the damage to be undone and many have directed their 15 minutes of Internet rage at the laptop manufacturer.
Unsurprisingly, that included a group of hacktivists using the moniker 'Lizard Squad', who managed to take over the DNS of lenovo.com last night, thus sending visitors to the company's website to one controlled by the attackers instead. This isn't something one would normally pay a great deal of attention to, because it is fairly innocent as hacks go, and doesn't mean the hackers have obtained access to the victim's network.

However, what makes this case both interesting and worrying is that the attackers not only changed the DNS A record — which made the website point to a different IP address — but they did the same to the MX records. This caused all email to @lenovo.com email addresses to be sent to a server controlled by the attackers as well. The potential for damage in this instance is far greater, even if the emails posted as proof on the group's Twitter account don't exactly reveal trade secrets and, as Ars Technica writes, the DNS was restored fairly quickly.
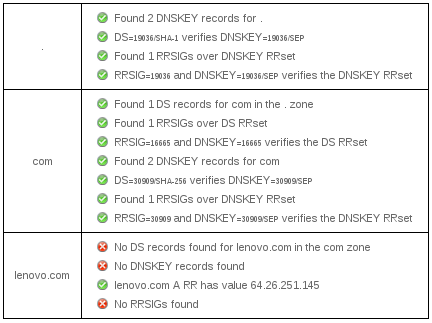
As domain hijacks have become fairly prevalent in recent years, and as rogue DNS servers and DNS cache poisoning mean one can never be absolutely certain that DNS responses are correct, DNSSEC is worth looking into. Though not a silver bullet against domain takeovers, and though it has strong opponents, it does sign DNS responses cryptographically. If Lenovo had used DNSSEC, and if a sender had verified the responses, email would not have ended up in the wrong hands.
At VB2014, CloudFlare researcher Nick Sullivan presented a paper on DNSSEC (also available as PDF here), that provides a very good introduction into the subject. You can also watch Nick's presentation on our YouTube channel.
Update: Several people have pointed out that hijacking a domain by gaining access to the registrar makes it trivial to get the new records signed by DNSSEC as well, making DNSSEC less suitable to contain the damage caused by domain hijacks.
Posted on 26 February 2015 by Martijn Grooten